A Practical Guide to Data Security Compliance for SMBs
Data security compliance is the official playbook for protecting sensitive information. It’s not just about digital locks and firewalls; it’s the entire system of rules, policies, and proactive IT management your business follows to keep customer, financial, and internal data safe from harm.
Turning Data Security Compliance into a Competitive Advantage
Many small and mid-sized businesses view compliance as a chore—another box to tick to stay out of trouble. But that’s a missed opportunity. When you build a strong compliance posture, you're actually creating a powerful asset that builds customer trust, strengthens your operations, and gives you a competitive edge. Partnering with a Managed IT Services provider (MSP) turns this complex requirement into a streamlined, automated process.
A solid compliance framework is a clear signal to your clients that you take their privacy and security seriously. This kind of reputation doesn't just keep your current customers happy; it can unlock doors to new markets and bigger partnerships.

Here’s how it translates into a real-world advantage for your business:
- Builds Unbreakable Trust: Compliance shows your clients you’re transparent and accountable with their data.
- Avoids Crippling Fines: Sticking to regulations like HIPAA, GDPR, or CMMC helps you sidestep penalties that can be devastating for a small business.
- Ensures Business Continuity: Proper policies and robust data backups mean you can keep the lights on even when a security incident occurs.
- Sets You Apart from the Pack: A "compliance-certified" badge can be an incredibly effective marketing tool that your competitors might be overlooking.
Gaining an Edge in Local Markets
Let’s look at a real example. A regional law firm in Dallas was able to land a major European client specifically because they had implemented strict GDPR controls with the help of their MSP. Their proactive, documented commitment to compliance was more persuasive to the client than a lower price tag.
In another case, a Memphis-based retailer emphasized its CMMC readiness when bidding for a contract with a defense supplier. Their MSP provided the necessary vulnerability assessments and documentation, which boosted their proposal success rate by 20%.
Key takeaway: Investing in compliance isn't just an expense. It's an investment in trust, resilience, and long-term risk reduction.
You can learn more about how small and mid-sized businesses in Dallas are using proactive IT support to nail their compliance requirements.
Real Business Outcomes
A local healthcare clinic recently dodged a potential $200,000 penalty by overhauling its data handling policies ahead of an audit. They worked with their managed services provider to automate endpoint encryption, conduct vulnerability assessments, and set up regular access reviews.
This proactive stance didn't just save them from a fine; it also slashed their incident response time in half. That quick action, enabled by their MSP's monitoring tools, was crucial for maintaining patient trust and avoiding any disruption to their services.
The Path to Operational Stability
At its core, data security compliance is about protecting your finances and ensuring your business continuity. A single data breach can cause costly downtime, regulatory fines, and a mass exodus of clients.
The key is to implement clear policies, perform regular risk assessments, and establish a robust disaster recovery plan. An MSP can help you conduct consistent reviews and testing to keep your processes aligned with ever-changing regulations without overwhelming your team.
Core Components of a Compliance Framework
So, what does a good framework actually look like? It usually boils down to four key pillars that a managed IT services partner can help you build and maintain:
- Policies and Procedures: This is your rulebook. It clearly documents how data is collected, where it's stored, and who can access it.
- Risk Assessments: You can't protect against threats you don't know exist. Regular vulnerability assessments help you find security gaps and prioritize what to fix first.
- Security Awareness Training: Your team is your first line of defense. Training teaches them how to spot threats like phishing and follow secure procedures.
- Continuous Monitoring: Using automated tools like Endpoint Detection and Response (EDR) to watch over your network helps you catch potential issues before they escalate into full-blown crises.
Partnering with an MSP brings all these components together seamlessly. They can handle the monitoring, risk assessments, and policy updates, freeing you up to focus on growing your business.
Instead of seeing compliance as a burden, start treating it as a strategic tool for building a more stable and trustworthy business. Customers absolutely notice the companies that go the extra mile to protect their information.
While small businesses often worry about the cost, proactive compliance almost always saves money in the long run. For instance, clients who maintain clear audit logs and have tested disaster recovery plans can significantly reduce investigation fees and recover from incidents much faster and more securely.
Now that we've covered the "why," let's dive into the "what." Next, we’ll break down major regulations like GDPR and HIPAA that you need to get right.
Untangling the Web of Key Compliance Regulations
The world of data security compliance can feel like drowning in a sea of acronyms. But you don't need a law degree to get a handle on the rules that affect your business. Think of regulations like HIPAA, GDPR, and CMMC as specific playbooks designed to protect different kinds of sensitive information. Figuring out which playbook you need to follow is the first, most crucial step.
For instance, a local clinic in Dallas is bound by the Health Insurance Portability and Accountability Act (HIPAA). This means every shred of patient data—from appointment notes in their medical documentation software to billing records—must be encrypted, stored securely, and locked down from unauthorized eyes. It's a heavy lift, which is why many turn to specialized IT support for healthcare providers in Dallas to manage their layered security and endpoint protection.
Now, picture a small e-commerce shop based in Memphis that happens to have customers in France. That shop falls under the General Data Protection Regulation (GDPR). Even without an office in Europe, just selling to EU residents means they have to get clear consent before collecting any personal data and must give customers an easy way to erase their information if they ask. An MSP can help configure their cloud solutions to meet these specific data residency and privacy requirements.
The Big Three You Can't Ignore
While there are dozens of regulations out there, a few heavy hitters impact most small and mid-sized businesses. Each has a different mission, whether it's protecting health records or securing data for government contracts. One thing is certain: you can't just ignore them. The penalties are getting too steep.
Make no mistake, the global trend is toward locking down data privacy. By the end of 2024, data privacy laws had expanded to cover 79% of the world's population, with 144 countries putting their own rules on the books. And these regulations have teeth—the EU alone slapped companies with €2.1 billion in fines in 2024 for GDPR violations.
Let's break down the regulations you're most likely to encounter:
HIPAA (Health Insurance Portability and Accountability Act): This one is for any organization in healthcare, plus any business partners they work with. It demands strict rules for protecting Protected Health Information (PHI) and requires regular risk assessments, tight access controls, and a clear plan for notifying patients if a breach happens.
GDPR (General Data Protection Regulation): This landmark EU regulation protects the personal data of its citizens. It applies to any business, anywhere in the world, that processes data from EU residents. Key principles include "data minimization" (only collect what you absolutely need) and the "right to be forgotten."
CMMC (Cybersecurity Maturity Model Certification): If you're a contractor or subcontractor for the Department of Defense, this one's for you. CMMC is a tiered certification system designed to prove you meet the government's cybersecurity standards for handling sensitive information.
Key Data Security Compliance Regulations at a Glance
To help you quickly see where your business might fit, the table below offers a simple side-by-side comparison of these major frameworks. It breaks down who each one applies to and what they fundamentally require, giving you a solid starting point for building your compliance strategy.
Think of this as your cheat sheet. While the details can get complex, understanding the core purpose of each regulation is the first step toward building a data security plan that not only protects your customers but also protects your business from costly mistakes.
The Real-World Cost Of A Compliance Failure
Skipping data security compliance isn’t just a technical oversight. It’s a direct hit to your finances and your reputation.
When those safeguards falter, the fallout isn’t an abstract warning. Real expenses pile up like dominoes, and small or mid-sized businesses often take years to recover.
Regulators don’t send courtesy notices. Break HIPAA, GDPR or CMMC rules, and fines can land in the six or seven figures—and that’s only the beginning.
The Snowball Effect of a Single Incident
Once the initial penalty hits, costs multiply at every turn. Here’s where the true damage of a compliance lapse shows itself:
- Legal And Consulting Fees: You’ll need attorneys and cybersecurity specialists to investigate the breach—often at premium rates.
- Customer Notification Costs: Regulations typically require notifying each affected person, which means printing, postage and administrative labor.
- Credit Monitoring Services: To rebuild trust, you may have to offer a year (or more) of credit monitoring for everyone impacted.
- Operational Downtime: Your team shifts focus from growth to crisis management, stalling projects and revenue.
Consider these industry averages: a single data breach now costs $4.44 million globally, and incidents involving stolen credentials take an average of 292 days to identify and contain. If you’re already short on cybersecurity talent, breach costs spike by 20 percent. For a deeper dive, see the full report on breach costs.
A Cautionary Tale: A Mid-Sized Logistics Firm
Imagine a Dallas-area logistics company handling sensitive shipping manifests for a major manufacturer. A misconfigured cloud server—an oversight their internal team missed—left unencrypted client data exposed, and an attacker moved in quickly.
The aftermath was swift and brutal:
The firm was hit with a $250,000 regulatory fine for failing to protect PII. They also spent over $80,000 on forensics, legal counsel and mandatory customer notifications.
Worse still, their largest client terminated a multi-year contract the moment they learned of the breach. Within six months, the total hit—including lost business—topped $500,000. Proactive monitoring from an MSP and a proper disaster recovery plan could have prevented the exposure and minimized the financial damage.
This scenario drives home a simple truth: investing in proactive compliance—ideally with a Managed IT Service Provider (MSP)—is far more cost-effective than shouldering the devastating expense of a failure.
Your Practical Roadmap to Achieving Compliance
Feeling overwhelmed by data security compliance? You're not alone. It’s easy to look at the regulations and see a mountain of work. But the key is to stop seeing it as one massive project and start treating it as a series of manageable steps.
This roadmap breaks it all down. It's an actionable framework any small or mid-sized business can follow, turning a complex challenge into a core business strength. With a systematic approach from a trusted IT partner, compliance becomes less about stress and more about a clear plan to protect your business and your clients.
Step 1: Identify and Classify Your Data
You can't protect what you don't know you have. The first real step is a deep dive to map out every piece of sensitive information your business collects, stores, and sends. Think of it like taking inventory of your most valuable assets. An MSP can use specialized tools to scan your network and cloud environments to find sensitive data you might not even know exists.
This means figuring out what types of data you handle and sorting them by how sensitive they are:
- Public Data: Stuff that’s meant to be seen, like marketing copy on your website.
- Internal Data: Business operational info that isn't for public eyes but wouldn't cause a crisis if it leaked.
- Confidential Data: This includes employee records, financial reports, or client contracts. A leak here would be very painful.
- Restricted Data: This is the crown jewels. We're talking about Protected Health Information (PHI), credit card numbers (PCI), or government-related data. This stuff is heavily regulated for a reason.
Once you know what data lives where, you can stop guessing and start focusing your security efforts where they matter most.
Step 2: Conduct a Comprehensive Risk Assessment
With your data all mapped out, it’s time to find the weak spots. A risk assessment is just a methodical way of hunting for potential threats and vulnerabilities in your systems. It’s all about answering the tough questions: "Where are we exposed?" and "What are the real odds of a breach here?"
A proper risk assessment isn't about finding blame; it's about building a proactive defense. It gives you a clear, prioritized list of security gaps so you can allocate your resources to fixing the most urgent issues first.
This process, often led by an MSP, needs to cover everything from your network setup and endpoint patch management to employee access rights and your data backup strategy. For a solid, structured approach, our small business cybersecurity checklist can be a great starting point.
Step 3: Implement Essential Security Controls
After you’ve identified the risks, you have to actually plug the holes. This is where you implement the layered security and procedural safeguards that form the backbone of your compliance strategy. These controls are the digital locks, security guards, and operational rules that protect your sensitive information.
Here are a few non-negotiables every SMB should have in place, which an MSP can manage for you:
- Encryption: Scramble your data so it's unreadable without a key. This applies both when it's sitting on a server (at rest) and when it’s being sent over the internet (in transit).
- Access Control: Give people access only to what they absolutely need to do their jobs. It’s called the principle of least privilege, and it’s a game-changer for security.
- Endpoint Protection: Every device—laptop, server, phone—needs modern protection like advanced antivirus and Endpoint Detection and Response (EDR). Automated patch management is just as important.
- Firewalls and Network Security: Think of this as your digital perimeter fence. It's there to block unauthorized traffic and keep an eye out for anything suspicious.
The infographic below shows exactly what happens when these controls fail. The financial fallout from a breach isn't just a single fine; it's a cascade of costs.
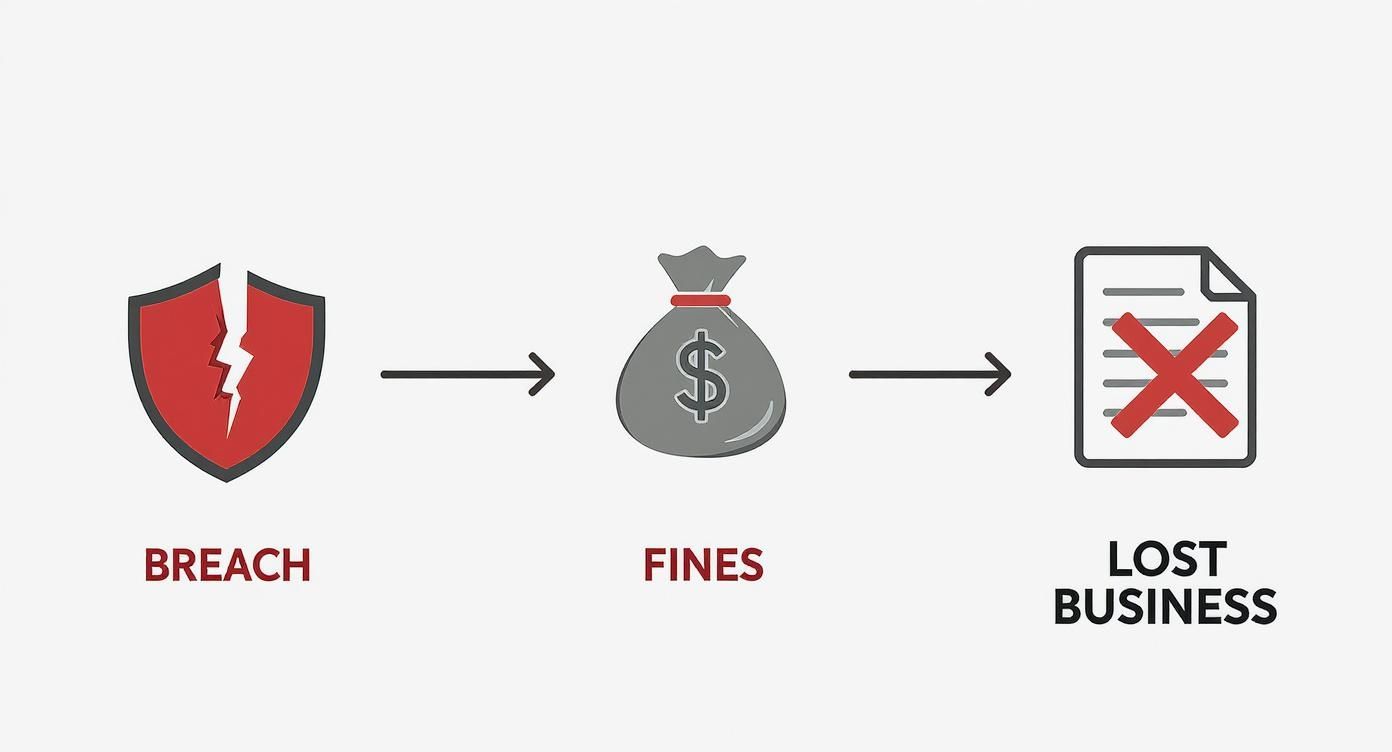
As you can see, one small failure can set off a chain reaction of devastating expenses, which really drives home the value of proactive, managed cybersecurity.
Step 4: Develop Clear Policies and Train Your Team
Here’s a hard truth: technology alone will never be enough. Your security controls have to be backed up by clear, documented policies that spell out the rules for everything from data handling to responding to a security incident. These policies, often developed with your MSP, are the playbook for your employees, making sure everyone knows their role in protecting company data.
A crucial part of your policy should cover what happens when tech gets old. A comprehensive guide for protecting sensitive data during electronics recycling can help ensure your data doesn't walk out the door with old hardware.
Finally, train your people. And then train them again. Regular security awareness training turns your team from a potential weak link into your best line of defense against ever-present threats like phishing and social engineering.
How Managed IT Services Simplify Compliance
Data security compliance isn't a "set it and forget it" project. It's an ongoing commitment that requires constant attention and deep expertise. For most small and mid-sized businesses, this endless cycle of monitoring, patching, and reporting just isn't sustainable with an internal team alone.
This is exactly where a Managed IT Service Provider (MSP) steps in. They become a critical partner, taking what feels like a daunting obligation and turning it into a manageable, automated process. Think of an MSP as your dedicated compliance engine, handling all the background work—from endpoint management to disaster recovery testing—needed to keep your business protected and in line with regulations.
From Reactive to Proactive
One of the biggest shifts an MSP brings is moving you away from the old "break-fix" IT model. Instead of waiting for something to go wrong, they put 24/7 remote monitoring and automated systems in place to catch problems before they can ever become compliance violations.
This proactive stance is non-negotiable today. In 2024 alone, researchers found over 30,000 new security vulnerabilities worldwide, a 17% jump from the previous year. Proactive defense isn't just a good idea; it's a financial necessity. You can discover more critical compliance stats for 2025 to see the full picture.
So, how do they do it? Key managed services include:
- Automated Patch Management: Making sure every piece of software and all your systems are updated with the latest security patches to seal off known weak points.
- Continuous Vulnerability Scanning: Regularly sweeping your network and devices to find and fix potential holes before a hacker can exploit them.
- Secure Data Backups and Recovery: Setting up and testing robust backup solutions to ensure your data is safe and can be restored quickly—a fundamental requirement for business continuity.
A Real-World Example in Financial Services
Imagine a mid-sized financial services firm in Dallas. Their small in-house IT team was swamped trying to keep up with tough industry rules. They were drowning in security reports, risk assessments, and threat alerts. Every hour they spent on compliance was an hour they weren't helping clients.
They adopted a co-managed IT model, partnering with an MSP to handle cybersecurity and compliance. The provider rolled out a powerful security information and event management (SIEM) system that automated threat detection. They also set up quarterly vulnerability scans and delivered clean, detailed reports that made auditors happy with almost zero effort from the firm's team.
The result? The firm confidently met all its compliance requirements. Better yet, their internal team was freed up to focus on strategic projects that grow the business. The co-managed partnership turned a massive operational headache into a real strategic advantage.
The Strategic Value of an MSP Partnership
A good MSP does more than just fix computers. They offer strategic IT consulting, making sure your technology not only supports your business goals but also meets all your regulatory demands. You get access to an entire team of cybersecurity and compliance specialists for a fraction of what it would cost to hire them yourself.
Our guide on IT managed services dives deeper into how this partnership gives you enterprise-level tools and expertise at a predictable cost.
When you entrust your data security compliance to an expert partner, you get something invaluable: peace of mind. It gives you the freedom to get back to what you do best—running your business.
Building a Security-First Company Culture
You can have the most advanced firewalls, the strongest encryption, and top-of-the-line endpoint protection, but all of it can be undone by a single, accidental click. This is exactly why a strong security culture isn't just a nice-to-have; it's absolutely essential for achieving genuine data security compliance.
Think of it this way: technology is only one part of the equation. Your team is your most critical security asset, and their daily habits are what ultimately decide whether your defenses hold strong or fall apart. A security-first culture flips the script, turning your biggest potential vulnerability—human error—into your strongest layer of defense. It gets everyone to stop thinking of security as "the IT guy's problem" and start seeing it as a shared responsibility.

From Training Checkbox to Lasting Reflex
Let's be honest, most security training is a once-a-year video that everyone forgets. That approach doesn't work. The goal is to build lasting security reflexes through continuous, engaging education, arming your team with the practical skills to spot and react to real-world threats.
Consider a property management company in Memphis that was getting hammered by phishing emails cleverly disguised as urgent maintenance requests. We helped them roll out regular, simulated phishing campaigns. The results were stunning: their click-through rate on malicious links plummeted by over 80% in just six months. Their employees learned to spot the subtle red flags, turning a high-risk situation into a routine defense drill.
Investing in your people's security knowledge is the single most effective way to strengthen your compliance posture. A well-trained team acts as a human firewall, actively detecting and reporting threats before they can cause damage.
So where should you focus your efforts for the biggest impact? Start here:
- Phishing Identification: Train everyone on how to spot the tell-tale signs of a scam—suspicious links, spoofed email addresses, and those out-of-the-blue requests for money or information that create a false sense of urgency.
- Strong Password Hygiene: This is non-negotiable. Enforce the use of unique, complex passwords and, most importantly, multi-factor authentication (MFA) across every single company application.
- Secure Data Handling: Create crystal-clear rules for how your team shares, stores, and gets rid of sensitive data, whether it's sitting in the cloud or on a laptop.
Making Security Culture Stick
Creating this kind of security-first mindset isn't a one-and-done project. It requires consistent effort and, crucially, buy-in from leadership. It has to become a core part of how your company operates every single day.
To make sure these practices are effective and don't just fade away, many businesses turn to structured programs. It’s worth exploring how professional security awareness training in Dallas, TX, can give you the tools and expertise to build an engaged, security-conscious team. When you make security a visible and valued part of your company culture, you're building a resilient organization that’s truly ready to meet its data security compliance obligations head-on.
Answering Your Top Data Compliance Questions
When it comes to data security compliance, it's easy to feel overwhelmed. Business owners are often juggling a dozen priorities, and figuring out these complex rules can feel like one more thing on a very long list. Let's tackle some of the most common questions we hear from businesses in Dallas and Memphis.
"My Business Is Small. Do I Really Need to Worry About This?"
Yes, absolutely. It's a common myth that only large corporations are on the radar for cyberattacks or regulatory audits. In reality, attackers often see smaller businesses as easier targets precisely because they assume security is weaker.
Regulations like HIPAA or PCI DSS (the standard for handling credit card information) don't care about your company's size; they care about the type of data you handle. A compliance slip-up can lead to fines that are genuinely crippling for a small business. Think of it this way: proactive compliance isn't just an expense—it's a critical investment in keeping your doors open.
"What’s the Best First Step to Get Started?"
The single most effective first step is a professional risk assessment. You can't protect what you don't know you have. Before spending a dime on new software or policies, you need a clear picture of what sensitive information you collect, where it lives, and which regulations apply to your specific situation.
A great managed IT services provider can perform a deep dive into your systems. They'll map out how your data moves, pinpoint your biggest compliance gaps and security holes, and give you a straightforward, prioritized plan to get things right without the guesswork.
"Can I Just Handle This Myself?"
While you technically could, it's a massive undertaking for most small businesses. The world of data security regulations is always changing. Keeping up with new threats, security patches, constant monitoring, and the mountain of required documentation is a full-time job in itself.
Partnering with an MSP instantly gives you a team of specialists and access to the kind of security tools that are typically out of reach for smaller companies. It's almost always more cost-effective than hiring an in-house compliance expert, and it ensures critical details don't get missed. This lets you and your team get back to focusing on what you do best—running your business.
Don’t let compliance become a source of stress. PWR Technologies provides expert guidance and managed IT services to help businesses in Dallas and Memphis achieve and maintain a strong security posture. Contact us today to simplify your data security compliance journey.




