What Is Zero Trust Security and Why It Matters for Your Business
At its heart, Zero Trust Security is a mindset shift built on a simple, powerful rule: never trust, always verify. It throws out the old-school notion that anything inside your network is automatically safe. Instead, it demands that every single user and device prove they are who they say they are—every time they try to access anything.
Moving Beyond the Castle-and-Moat Mentality
For decades, businesses treated cybersecurity like building a medieval castle. They put up a strong outer wall—a "moat" of firewalls and antivirus software—and assumed everyone inside was a trusted friend. If you were inside the fortress, you had free rein.
But that model is broken. Today, your company’s data doesn't live in one neat castle anymore. It's scattered across cloud apps like Microsoft 365, accessed by your team working from their homes in Dallas, and shared with partners in Memphis. The old perimeter has vanished, and that makes the castle-and-moat defense dangerously obsolete. A single stolen employee password can be the key to the entire kingdom.

A New Philosophy: Assume Breach
Zero Trust completely flips the script. It starts with the assumption that a threat is already inside your network, or that a trusted employee's login details have been compromised.
Think of it like a secure government building. Your ID badge might get you through the front door, but it won’t let you wander into any office you please. At every checkpoint—every secured room, every classified file cabinet—you have to swipe your badge again to prove you belong there.
This constant, relentless verification is the soul of Zero Trust. It scrutinizes every access request as if it’s a potential attack until it's proven otherwise. This is a huge deal for a small business because it dramatically shrinks the "blast radius" if a breach does happen. By containing threats, you can avoid a minor incident turning into a company-wide disaster that disrupts operations for days.
This approach strengthens fundamental network security best practices by creating multiple internal checkpoints. Even if an attacker gets past the first line of defense, they're stopped cold at the next one.
To make this crystal clear, let's look at a side-by-side comparison.
Traditional Security vs Zero Trust At a Glance
This table breaks down the fundamental differences between the outdated security model and the modern Zero Trust approach that proactive IT support enables.
As you can see, the shift isn't just about new tools; it's a complete change in how we think about protecting our most valuable business assets.
The Three Pillars of a Zero Trust Strategy
Zero Trust isn't a single piece of software you can just install and forget. It's a strategic framework built on three core principles. Once you understand these pillars, you'll see how Zero Trust moves from a buzzword into a practical way to protect your business from modern threats like ransomware.
This infographic gives a great visual breakdown of how it all fits together.
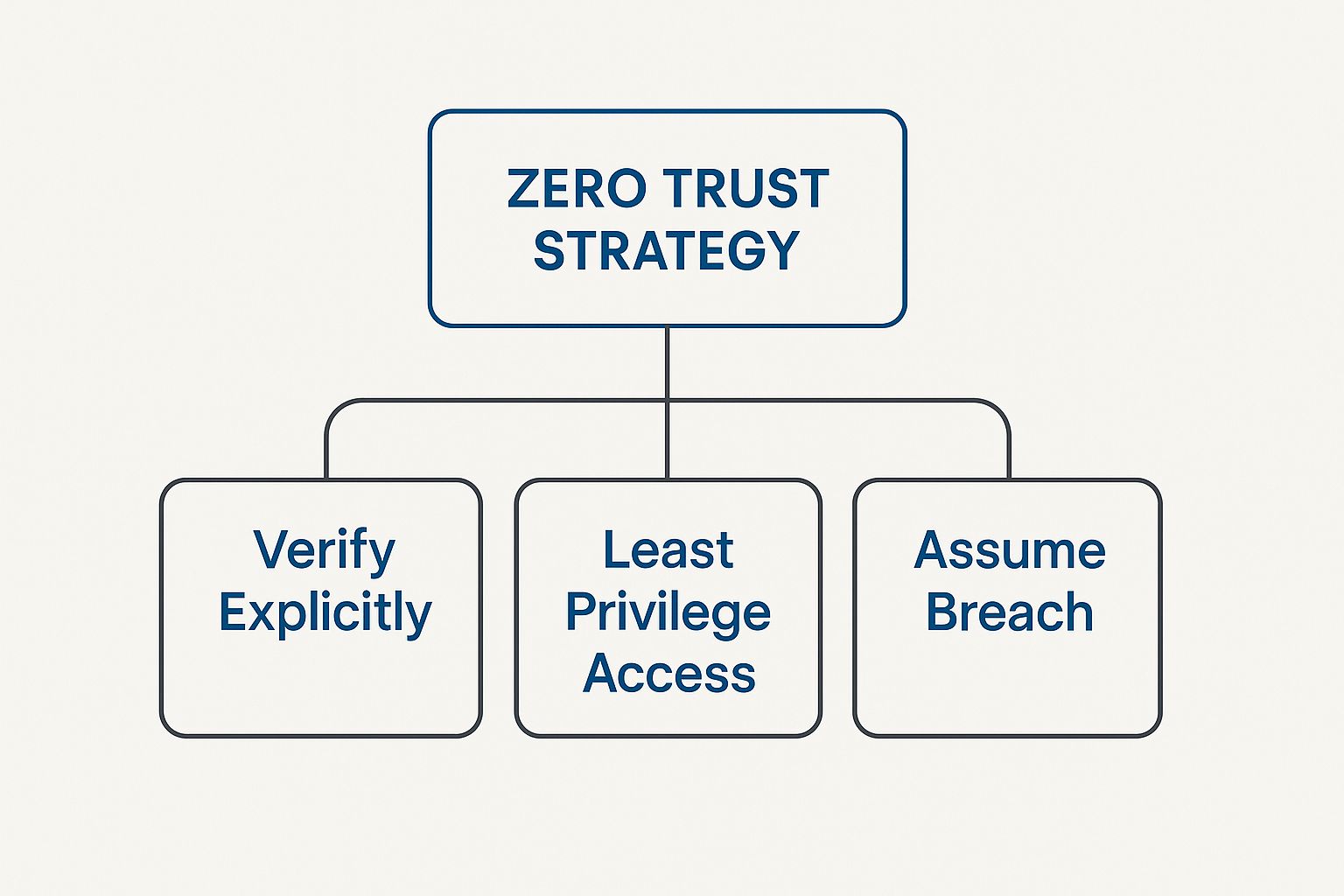
As you can see, these pillars aren't standalone concepts. They're designed to work in concert, creating a security posture that constantly adapts to new information and potential threats.
Verify Explicitly
The first pillar, Verify Explicitly, is all about leaving no stone unturned when someone tries to access your network. You have to authenticate and authorize every request based on all the data you have available. A username and password simply aren't enough anymore.
For a small business, this means the system should be asking more questions. Where is the user logging in from? Is the device they're using secure and up-to-date? What service are they trying to access?
Practical Example: An employee at a Memphis accounting firm logs in from their company laptop at 10 AM. This looks perfectly normal. But if those same credentials are used five minutes later from an unrecognized device in a different country, a Zero Trust system sees that as a massive red flag. Access would be blocked instantly, preventing a hacker from accessing sensitive client financial data. It's this kind of dynamic, context-aware checking that shuts the door on unauthorized access.
Use Least-Privilege Access
Next up is Use Least-Privilege Access. The idea here is simple but incredibly powerful: only give people access to the specific information and tools they absolutely need to do their jobs. Nothing more. It's the digital equivalent of giving someone a key to their own office, not a master key to the entire building.
This one principle can dramatically shrink the potential damage if an account ever gets compromised. If a hacker gets into a marketing coordinator's account, they shouldn't be able to access your financial records or critical server settings. A Managed IT provider is essential for correctly setting up and auditing these permissions across all your systems, ensuring business continuity. Constantly monitoring access is also a huge part of Zero Trust, which is where technologies like ethical AI for insider threat detection can make a real difference.
Assume Breach
Finally, the third pillar, Assume Breach, forces a fundamental change in your security mindset. You stop focusing solely on keeping attackers out and start operating as if they're already in. You accept that a breach is a matter of when, not if. This proactive thinking pushes you to design your network to limit the "blast radius" of any incident.
This philosophy is about building resilience. The goal is to create a system that can take a hit, contain the damage, and keep the business running. It puts the focus on fast detection, immediate response, and quick recovery—all cornerstones of effective disaster recovery planning.
This is where technologies like network segmentation and advanced Endpoint Detection and Response (EDR) become critical. They help you wall off threats to a small corner of your network and give you the tools to snuff them out before they can spread. Adopting this mindset means you are prepared to mitigate threats quickly, minimizing downtime and protecting your bottom line.
Why Zero Trust Is a Game-Changer for SMBs
It's a common misconception that sophisticated cybersecurity is only for massive corporations. But for small and mid-sized businesses in Dallas and Memphis, a Zero Trust approach isn't just a good idea—it's crucial for survival. Cybercriminals often go after SMBs specifically, thinking they're easier targets with weaker defenses.
Zero Trust completely changes that dynamic. Instead of just guarding the front door, this model treats every request to access data as a potential threat. It challenges and verifies everyone and everything, making it incredibly difficult for a hacker to move around your network, even if they manage to steal a password. This is more important than ever as teams work from anywhere, using home networks and personal devices to connect to sensitive company files.

From Cost Center to Competitive Advantage
Think of Zero Trust not as a cost, but as a strategic investment in your business's continuity and reputation. It’s about fiercely protecting what matters most: your customer data, your financials, and the trust you've worked so hard to build.
The market is waking up to this reality. The global Zero Trust security market was valued at USD 36.96 billion and is expected to explode to USD 92.42 billion by 2030. This isn't just random growth; it's driven by the exact trends hitting SMBs, like migrating to cloud solutions and the constant threat of ransomware. You can read the full analysis on this market growth to see the numbers for yourself.
This proactive approach to security becomes a powerful selling point. When you can confidently tell clients their information is protected by a modern, rigorous security model, you build the kind of trust that wins and keeps business.
A Real-World Example in Dallas
Let's look at a real-world scenario. A mid-sized professional services firm in Dallas recently worked with their Managed IT Services provider to adopt Zero Trust principles. Not long after, an employee received a sophisticated phishing email that looked exactly like an invoice from a trusted vendor. They clicked the link, and it took them to a fake login page for their Microsoft 365 account.
In an old-school security setup, this one slip-up would have been a disaster. The attacker could have gained access to the employee's email, files, and contact lists, opening the door for a full-blown ransomware attack or a massive data breach that could halt business operations.
But because the firm had a Zero Trust policy, the story had a very different ending. The login attempt from an unknown device in a strange location was instantly flagged. Multi-factor authentication (MFA) kicked in, sending a notification to the employee's phone. They knew it wasn't them, denied the request, and the system automatically blocked the attacker.
The managed IT team got an alert and immediately initiated their incident response plan, ensuring the threat was neutralized before it could do any damage. This is a perfect example of how the right security layers, including knowing the best firewalls for small business, work together. This proves that smart security isn't just an expense—it's an investment that saves your reputation and your future.
Building Your Zero Trust Architecture
So, how do you go from the idea of Zero Trust to a real-world security setup? It's not about buying a single, magical "Zero Trust box." Instead, it's about layering several smart technologies that all work together to enforce that core rule: never trust, always verify.
For a small or mid-sized business, this might sound daunting. But in reality, it's a logical process, and a good Managed IT Services partner can handle the heavy lifting. The goal is to build a system where every person, device, and connection has to prove it belongs before it gets anywhere near your important data. This isn't just good practice; it's a vital part of modern data security and compliance.
Identity and Access Management: The New Gatekeeper
If you're going to start anywhere, start here. Identity and Access Management (IAM) is the absolute cornerstone of a Zero Trust model. Think of IAM as the central command center for your security, figuring out who is allowed to access what—and why. We've moved way past just a simple username and password.
A huge piece of the IAM puzzle is Multi-Factor Authentication (MFA). This is your first and most powerful line of defense. It simply means a user has to provide at least two pieces of evidence to prove they are who they say they are—their password plus a code from an authenticator app, for example. This one step is proven to block over 99.9% of attacks that rely on stolen credentials. An MSP can get MFA rolled out correctly across all the tools you rely on, from Microsoft 365 to your accounting software, strengthening your security posture overnight.
Securing Every Endpoint
In the Zero Trust world, we don't trust any device automatically. Every laptop, smartphone, or server trying to access your network is an "endpoint," and each one is a potential doorway for an attacker. That means securing them is not optional.
This is more than just running basic antivirus software. Real endpoint security means constantly checking the health of every device. Is its operating system up-to-date? Are security patches installed? Is any unusual software running in the background? If a device fails any of these checks, it gets blocked—even if the user has the right password. This is a fundamental part of good endpoint management in Dallas, TX because it stops a compromised device from ever touching your network.
By verifying both the user and the device, you create a powerful one-two punch. A legitimate user on a compromised laptop is just as dangerous as a hacker on a secure one. Zero Trust blocks both.
Containing Threats with Network Segmentation
Finally, let's talk about containing the damage if something does go wrong. Network segmentation is a strategy where you chop your network up into smaller, isolated zones. It’s like the watertight compartments in a ship—if one area gets flooded, the doors seal and the rest of the ship stays safe.
Applied to your IT, this means a hacker who breaches one area, like the guest Wi-Fi, is stuck there. They can't move sideways to get to your file servers or customer database. This "least privilege" approach is applied to the network itself, massively reducing the blast radius of any potential breach and forming a key part of your business continuity plan. A managed IT partner can design this segmentation to make your entire infrastructure far more resilient.
A Practical Roadmap to Adopting Zero Trust
https://www.youtube.com/embed/I-oTQFsK3Es
Getting started with Zero Trust isn't about flipping a switch overnight. Think of it as a journey, not a destination. For most small and mid-sized businesses, the smart play is to start small by focusing on what matters most and then building out from there. A phased approach, guided by an IT partner, delivers real security wins right away and helps you build momentum for the long haul.
This roadmap is designed to be practical, avoiding overwhelming complexity to focus on steps that give you the biggest security return on your investment.
Phase 1: Identify and Protect Your Crown Jewels
First thing's first: you can't protect what you don't know you have. Work with your IT provider to identify your "crown jewels"—the data, systems, and applications that are absolutely essential for you to operate. This might be your customer database, your financial records, or sensitive intellectual property stored in cloud solutions.
Once you know what’s most important, the goal is to lock it down. This is where you put your foundational Zero Trust controls in place:
- Enforce Multi-Factor Authentication (MFA): This is non-negotiable. Before you do anything else, turn on MFA for every single account that has access to your critical data, especially for cloud platforms like Microsoft 365. It remains the single most effective way to stop password-based attacks.
- Strengthen Endpoint Security: Every laptop, desktop, and server that touches your critical assets needs modern endpoint protection and monitoring. This means deploying endpoint detection and response (EDR) solutions that can actively hunt for threats, not just react to known viruses.
Client Scenario: A Memphis-based logistics company started their Zero Trust journey by focusing solely on their Microsoft 365 environment, where all their client contracts and communications lived. Working with their MSP, they had MFA rolled out to all users and EDR deployed on every company device within the first month. This simple, focused first step immediately reduced their risk of a business-crippling data breach.
Phase 2: Implement Least Privilege and Segmentation
With your most valuable assets better protected, the next move is to limit the blast radius if an attacker does find a way in. This is all about containment—making it harder for threats to spread across your network and ensuring business continuity.
This is where the principle of "least privilege" comes in. Your IT partner will review and adjust user permissions to ensure employees only have access to the specific information and tools they absolutely need to do their jobs, and nothing more.
At the same time, you can begin to segment your network. Think of this as building digital walls inside your office. Your guest Wi-Fi, for instance, should be completely walled off from the network your team uses to access company data.
By taking these steps, that same Memphis firm dramatically shrank its attack surface. This wasn't just a security win; it was a business win, too. Six months later, they were able to show their insurance provider a clear plan for managing risk, which helped them secure more favorable cyber insurance premiums. Their story is a perfect example of how a step-by-step, managed approach makes Zero Trust a realistic and valuable goal for any business.
How Managed IT Services Make Zero Trust Achievable
Let's be honest. For most small and mid-sized businesses, building a full-blown Zero Trust security framework from scratch is intimidating. It demands deep security know-how, specialized tools, and 24/7 monitoring—resources that most companies simply don't have in-house.
This is where a good Managed IT Services Provider (MSP) changes the game. Think of an MSP as your dedicated security partner, bringing enterprise-level protection within reach without the hefty price tag of hiring a full-time cybersecurity team.
The Expertise and Tools You Need
Putting Zero Trust into practice is more about smart strategy than just buying new software. A seasoned MSP brings a wealth of experience from working with hundreds of businesses, so they've seen it all. They know the specific threats targeting businesses in Dallas and Memphis and can turn the core ideas of Zero Trust into a practical, affordable plan for you.
Partnering with an MSP also gives you access to a powerful security arsenal that would be incredibly expensive to manage on your own.
- Advanced Threat Detection: MSPs use sophisticated tools like Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) to provide 24/7 monitoring and spot trouble before it starts.
- Proactive Patch Management: A huge part of verifying every device is keeping it updated. Your MSP automates this process through their endpoint management services, closing security holes before attackers can find them.
- Identity and Access Control: They'll set up and manage Multi-Factor Authentication (MFA) and enforce least-privilege access, ensuring people only have access to what they absolutely need.
An MSP essentially becomes your outsourced security operations team. They do the heavy lifting—the constant threat hunting, policy management, and incident response—so you can focus on what you do best: running your business.
A Practical Partnership for Growth
Working with an MSP takes the complexity out of strengthening your security. It starts with a detailed risk assessment to figure out where your most sensitive data lives. From there, they build a phased plan that respects your budget and addresses your biggest risks first. This is never a one-size-fits-all approach; it’s a strategy built just for you.
Imagine a healthcare clinic in Dallas needing to secure patient data to meet HIPAA compliance. An MSP might start by locking down the electronic health records system with strict access rules and MFA. Next, they could segment the network to keep medical devices separate, so if one device is compromised, the infection can't spread. This step-by-step method delivers immediate protection while building towards a complete Zero Trust environment.
This is the real power of IT managed services: they turn a complex security theory into a real-world defense that protects your business, your reputation, and your bottom line.
Ready to make enterprise-grade security a reality for your business? The team at PWR Technologies LLC has the expertise to design and manage a Zero Trust strategy that fits your unique needs. Contact us today for a consultation and discover how proactive IT support can protect your future.




