10 Network Security Best Practices to Protect Your Business
In today's hyper-connected business environment, your network's security is no longer a simple IT checklist item; it is a direct driver of business continuity and growth. For small and mid-sized businesses, particularly those in competitive markets like Dallas, TX and Memphis, TN, a single security incident can lead to crippling downtime, significant financial loss, and irreversible damage to client trust. The threats facing medical clinics, law firms, and financial services are more sophisticated than ever, demanding a shift from reactive problem-solving to proactive, strategic defense managed by experts. Ignoring this reality means leaving your most critical assets exposed.
This guide provides a detailed roadmap of 10 essential network security best practices designed to fortify your business. We move beyond abstract concepts to deliver actionable steps and real-world scenarios that demonstrate tangible value. You will learn how implementing layered defenses like Zero Trust Architecture, strengthening access controls with Multi-Factor Authentication, and empowering your employees through effective security awareness training can protect your operations. Each practice is a crucial component in building a resilient operational framework. By adopting these strategies, often with the guidance of a Managed IT Services partner like PWR Technologies, you can transform your network from a potential vulnerability into a secure, reliable foundation for sustainable growth.
1. Adopt a Zero Trust Architecture: Never Trust, Always Verify
The traditional "castle-and-moat" approach to network security, where everything inside the network is trusted, is dangerously outdated. A Zero Trust framework modernizes your security posture with a simple but powerful principle: never trust, always verify. This model assumes that threats can originate from anywhere, both inside and outside your network perimeter. For a small business, this means every user, device, and application must be rigorously authenticated and authorized before gaining access to your valuable data, whether they are in the office or working remotely.
This approach dramatically minimizes your attack surface. For example, a Dallas-based law firm using a Zero Trust model would require a lawyer connecting from a courthouse Wi-Fi to re-authenticate before accessing sensitive case files, containing any potential threat at the point of entry. Instead of a single breach giving an attacker free rein, a Zero Trust architecture contains threats by enforcing strict access controls at every connection point.
How Zero Trust Works in Practice
Implementing Zero Trust involves a continuous cycle of verification. This process flow diagram visualizes the core steps for securing every access request.
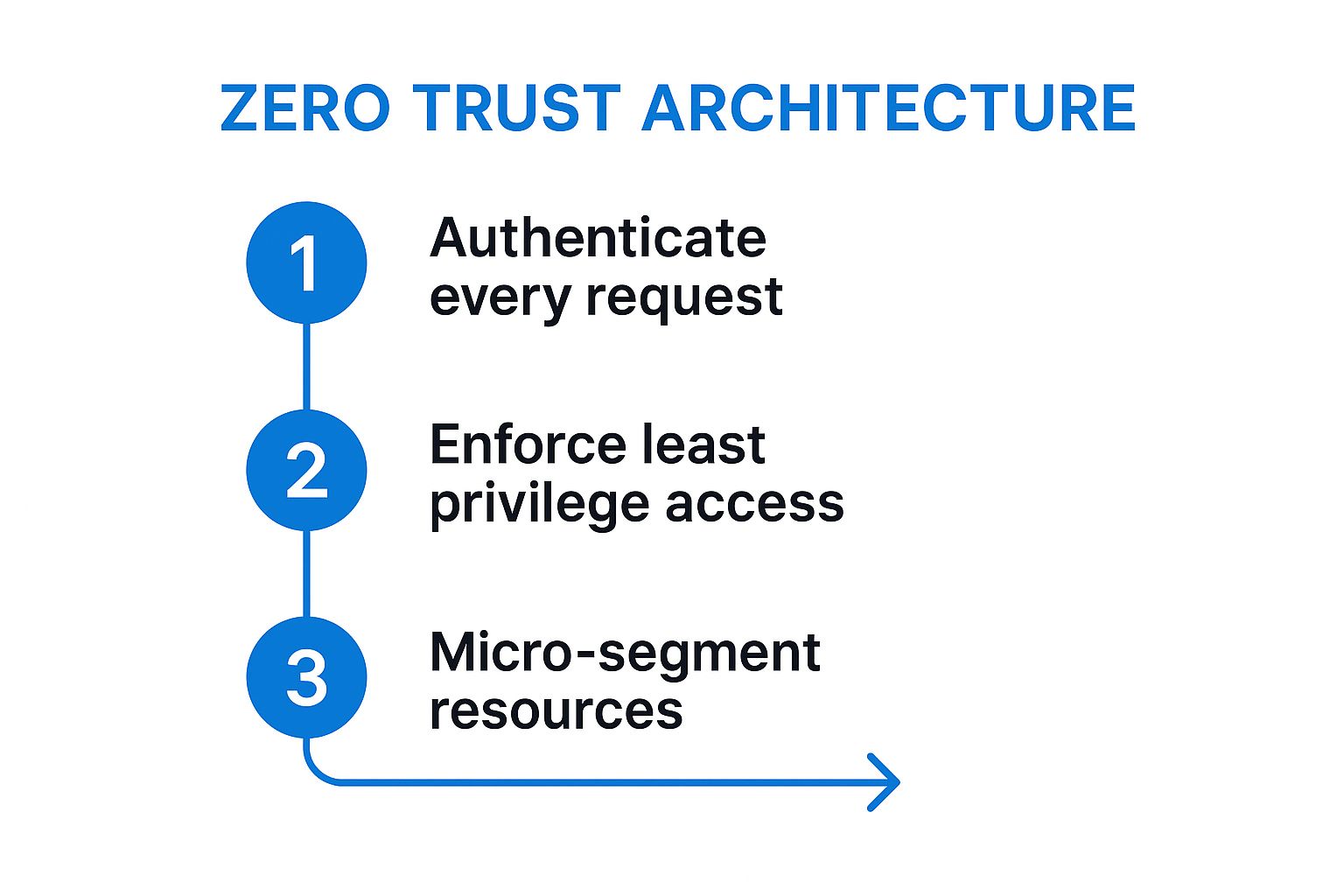
The diagram highlights that every request is first authenticated, then granted the minimum necessary permissions, and finally directed to a segmented resource, limiting potential breach impact.
Actionable Steps for SMBs
For an SMB, a complete overhaul isn't necessary. A phased rollout with a Managed IT Services Provider (MSP) is one of the most effective network security best practices.
- Start with Critical Assets: Identify your most sensitive data, such as financial records or client information, and apply Zero Trust principles there first.
- Implement MFA: Enforce multi-factor authentication across all services, especially for remote access to cloud platforms like Microsoft 365. This is your single most impactful first step.
- Segment Your Network: Use micro-segmentation to create small, isolated zones within your network. If one segment is compromised, the breach cannot easily spread to others.
- Enforce Least Privilege: Grant users and applications only the absolute minimum access required for them to perform their jobs.
This strategic shift prevents attackers from moving laterally within your network. For an in-depth exploration of this strategic approach, delve into a practical guide on Zero Trust Security. If you are ready to start your journey, you can learn more about how to implement a Zero Trust security model with a trusted partner.
2. Implement Multi-Factor Authentication (MFA): Your Strongest Access Guard
Relying on passwords alone is one of the most common yet riskiest security missteps a business can make. Multi-Factor Authentication (MFA) provides a critical layer of defense by requiring two or more verification factors to grant access. This approach combines something you know (a password), something you have (an authenticator app on your phone), and/or something you are (a fingerprint), making it exponentially harder for unauthorized users to compromise an account.
Implementing MFA is one of the most effective network security best practices for protecting your sensitive business and client data. Microsoft reports that MFA can block over 99.9% of account compromise attacks. A Memphis-based accounting firm that enables MFA for its cloud accounting software ensures that even if a password is stolen, cybercriminals cannot access confidential client financial data without the second verification step, preventing catastrophic fraud.

Actionable Steps for SMBs
Integrating MFA doesn't need to be disruptive. A strategic, phased rollout ensures a smooth transition for your team while immediately strengthening your security posture.
- Prioritize Privileged Accounts: Start by enforcing MFA for administrators and users with access to critical systems, such as network infrastructure, financial software, or patient records in a healthcare setting.
- Use Secure MFA Methods: Whenever possible, guide users toward authenticator apps (like Google Authenticator or Microsoft Authenticator) or physical hardware tokens. These are significantly more secure than SMS-based codes, which can be intercepted.
- Educate Your Team: Partner with an MSP to train employees to recognize and report "MFA fatigue" attacks, where attackers repeatedly send push notifications hoping a user will mistakenly approve one.
- Establish Clear Recovery Plans: Create and document a secure process for users who lose their MFA device. This ensures they can regain access without compromising security.
3. Implement Regular Security Patch Management: Close the Door on Known Threats
Leaving software unpatched is like leaving a key under the doormat for cybercriminals. Regular patch management is the critical process of identifying, testing, and installing updates to your software, operating systems, and firmware. This proactive practice, often managed by an IT service provider, addresses known security vulnerabilities before attackers can exploit them, forming a fundamental layer of your company's defense.
This isn't just a theoretical risk. The infamous WannaCry ransomware attack crippled hundreds of thousands of computers globally by exploiting an unpatched vulnerability in Windows. For a small business, a single unpatched server could lead to a complete operational shutdown. Proactive endpoint management that includes timely patching is a non-negotiable part of modern network security best practices.
How Patch Management Works in Practice
A successful patch management strategy is a continuous, systematic cycle, not a one-time task. It involves maintaining a complete inventory of all assets, scanning for missing patches, testing updates in a safe environment, and deploying them according to a set schedule. This structured approach, handled by a managed IT partner, minimizes both security risks and operational disruptions.
Actionable Steps for SMBs
For a small or mid-sized business, managing patches manually across all devices is inefficient and prone to error. Partnering with a managed IT services provider can automate and streamline this entire process.
- Establish a Full Asset Inventory: You can't protect what you don't know you have. An MSP can help you maintain a detailed, up-to-date inventory of all hardware and software.
- Prioritize Ruthlessly: Focus first on patches for critical vulnerabilities affecting internet-facing systems, servers, and software handling sensitive data.
- Test Before Deploying: Always test patches in a non-production environment or on a small group of non-critical systems to ensure they don't cause operational issues.
- Automate Where Possible: Use automated patch management tools to ensure consistent and timely deployment across all endpoints, reducing the window of opportunity for attackers.
4. Network Segmentation and Micro-Segmentation
Treating your entire network as one large, open space is a significant security risk. Network segmentation is a fundamental practice that divides your network into smaller, isolated subnets. This strategy ensures that if one part of the network is compromised, the breach is contained and cannot easily spread to other critical areas—a crucial layer in any modern cybersecurity defense.
This approach is like using bulkheads in a ship; a leak in one compartment doesn't sink the entire vessel. Consider a property management company in Dallas: segmenting the network ensures that a breach on the public Wi-Fi offered to tenants cannot compromise the internal network containing sensitive financial and resident data. The infamous 2013 Target breach, where attackers gained access to payment systems through a third-party HVAC vendor, is a stark reminder of the catastrophic consequences of a flat, unsegmented network.

How Network Segmentation Works in Practice
Micro-segmentation takes this concept a step further by creating secure zones around individual workloads or applications. This allows for highly granular security policies that control traffic between assets, even those within the same subnet. It's a key component of a Zero Trust strategy, effectively creating a secure, individualized perimeter for every critical application or data store.
Actionable Steps for SMBs
Implementing segmentation doesn't require a complete network redesign. A managed IT services provider can help you strategically phase in these protections as part of your infrastructure support.
- Map Your Assets: Begin by identifying all network assets and data flows. Understand what data is critical and where it resides.
- Segment Based on Risk: Create separate network segments for different functions. Isolate guest Wi-Fi, IoT devices, and point-of-sale systems from your core corporate network and sensitive servers.
- Control East-West Traffic: Don't just focus on perimeter defense ("north-south" traffic). Implement rules to control communication between servers and devices within your network ("east-west" traffic) to stop lateral movement.
- Implement for Compliance: Use segmentation to meet regulatory requirements. For example, medical clinics in Memphis can isolate systems containing Protected Health Information (PHI) to maintain HIPAA compliance.
5. Comprehensive Security Awareness Training
Technology alone cannot secure your network; your employees represent your first and most critical line of defense. Comprehensive security awareness training is an ongoing educational program that transforms employees from potential security risks into a vigilant human firewall. This proactive approach arms your team with the knowledge to recognize, avoid, and report cyber threats like phishing, directly strengthening your organization's security culture.
The human element is consistently a factor in data breaches, with the Verizon 2022 DBIR noting that 82% of breaches involve a human component. By investing in training, you directly address this primary attack vector. For instance, a small business that regularly runs phishing simulations can teach its finance team to spot fraudulent invoice emails, preventing a costly wire transfer to a cybercriminal and demonstrating a clear return on investment.
How Security Awareness Training Works in Practice
Effective training is not a one-time event but a continuous cycle of education, testing, and reinforcement. It builds a culture where every team member understands their role in protecting company data. To grasp the full scope of this crucial defense, understand what constitutes effective security awareness training. This ongoing process keeps security top-of-mind and adapts to evolving threats.
Actionable Steps for SMBs
For small and mid-sized businesses, building a strong security culture is an achievable and high-impact goal. A phased, consistent approach is far more effective than an annual check-the-box exercise.
- Implement Regular, Bite-Sized Training: Conduct short, engaging training sessions quarterly or monthly instead of a long annual seminar. This keeps information fresh and improves retention.
- Simulate Real-World Attacks: Use simulated phishing campaigns to test employees' awareness in a safe environment. Use the results to provide targeted, constructive feedback.
- Tailor Content to Roles: Customize training materials for different departments. For example, the finance team faces different threats than the sales team.
- Make Reporting Easy: Create a simple, clear process for employees to report suspicious emails or activities without fear of blame. Positive reinforcement encourages vigilance.
This strategy empowers your team, turning a potential weakness into a formidable asset. For expert guidance in building an effective program, you can learn more about comprehensive security awareness training in Dallas, TX from a trusted partner.
6. Implement Encryption for Data at Rest and in Transit
Simply having a firewall is not enough; true data protection means making your information unreadable to unauthorized parties, even if they breach your defenses. Encryption is a fundamental network security best practice that acts as your last line of defense. It converts sensitive data into a coded format, rendering it useless without the specific decryption key. For a professional services firm, this means protecting client contracts and financial data, whether it is stored on a server (at rest) or moving across the internet in an email (in transit).
This critical layer of IT security mitigates the impact of a physical theft or a network intrusion. If a company laptop is stolen from an employee's car, encrypted data remains secure and inaccessible, preventing a data breach and potential compliance violations. This is a non-negotiable standard for modern business operations.
How Data Encryption Protects Your Business
Encryption safeguards your data in two states: "at rest" when it is stored on devices like hard drives and servers, and "in transit" as it travels over networks like the internet or your local Wi-Fi. Applying encryption in both scenarios ensures comprehensive protection against unauthorized access at every stage of the data lifecycle.
Actionable Steps for SMBs
Integrating encryption doesn't require a complete IT overhaul. A strategic, phased approach can significantly bolster your security posture.
- Enforce Full-Disk Encryption: Use built-in tools like BitLocker for Windows and FileVault for macOS on all company laptops, servers, and mobile devices. This protects data if a device is lost or stolen.
- Secure Web Traffic with TLS: Ensure your website and all applications use Transport Layer Security (TLS) to encrypt data moving between a client and your server. This is essential for protecting login credentials and sensitive customer information.
- Encrypt Your Backups: Your backup data is a high-value target for attackers. Both on-site and cloud backups must be encrypted to prevent a single breach from compromising your entire business continuity plan.
- Manage Encryption Keys Securely: Store your encryption keys separately from the data they protect. An IT partner can help implement a formal key management policy that includes regular key rotation and documented recovery procedures.
7. Continuous Security Monitoring and Logging
You cannot protect against threats you cannot see. This is where continuous security monitoring and logging become indispensable network security best practices. This approach involves the real-time collection and analysis of security data from across your entire IT infrastructure. For a growing business, this means having a constant, vigilant eye on all network activity to detect threats, anomalies, and policy violations the moment they occur, often through a Security Operations Center (SOC) provided by an MSP.
This proactive stance transforms your security from a reactive, damage-control model to one of proactive threat hunting. Instead of discovering a breach months after the fact, continuous monitoring provides the visibility needed for rapid incident response. A real-world example is detecting multiple failed login attempts from an unusual location on a server at 3 a.m. and automatically locking the account, preventing a breach before it happens.
How Monitoring and Logging Work in Practice
Implementing a robust monitoring system centralizes security event data from servers, firewalls, endpoints, and cloud solutions like Microsoft 365. Advanced security tools like Endpoint Detection and Response (EDR) or Managed Detection and Response (MDR) then analyze this data to identify suspicious activity. This provides a unified view of your security posture, turning vast amounts of raw data into actionable intelligence.
Actionable Steps for SMBs
For an SMB, getting started with monitoring doesn't require an enterprise-level budget, especially when partnering with a co-managed IT services provider.
- Centralize Critical Logs: Start by collecting and centralizing logs from your most critical systems, such as domain controllers, firewalls, and key application servers.
- Log Important Events: Ensure you are logging all authentication attempts (both successful and failed), privilege escalations, and system configuration changes.
- Establish a Baseline: Monitor your network for a period to understand what normal activity looks like. This baseline is essential for accurately identifying anomalies that could signal an attack.
- Leverage an MSP's SOC: Partner with a managed services provider that offers 24/7 monitoring through a SOC. This gives you enterprise-level protection without the cost of an in-house team.
This methodical approach ensures you gain maximum visibility with minimal resource strain. For businesses in Dallas seeking to enhance their security posture, professional services can streamline this entire process. You can explore how to get started with proactive status monitoring and alerting to keep your operations secure.
8. Enforce the Principle of Least Privilege (PoLP)
Beyond firewalls and antivirus software, one of the most powerful network security best practices is controlling internal access. The Principle of Least Privilege (PoLP) is a foundational concept where users and systems are granted only the minimum permissions necessary to perform their legitimate tasks. This simple idea radically limits your exposure by assuming that any account could be compromised.
By restricting access rights, you contain the potential damage from a security incident. For example, an administrative assistant's user account should not have access to the company's core financial servers. If that assistant's account is compromised through a phishing email, the attacker's access is limited to non-critical files, preventing them from reaching sensitive data and crippling the business. This is a key part of IT security and risk management.
How PoLP Works in Practice
Implementing PoLP means shifting from a default "allow all" to a "deny all" mindset. Access is explicitly granted on a need-to-know basis, not as a matter of convenience. This ensures that employees, applications, and services have just enough access to function and no more, dramatically shrinking the internal attack surface. This proactive approach is a cornerstone of a robust security posture.
Actionable Steps for SMBs
Integrating PoLP doesn't require a complete overhaul; it can be implemented incrementally to strengthen your defenses.
- Start with Zero Access: When creating a new user account or deploying an application, begin with no permissions and add them one by one as function requires.
- Segment Administrative Accounts: Ensure administrators use a standard, non-privileged account for daily tasks like email and browsing. A separate, highly-secured account should be used only for administrative duties.
- Conduct Quarterly Access Reviews: Regularly audit user permissions across your network. Remove any privileges that are no longer required due to role changes or completed projects.
- Limit Access Temporally: For tasks requiring temporary elevated access, use solutions that grant privileges for a limited time and automatically revoke them afterward.
9. Conduct Regular Vulnerability Assessments and Penetration Testing
Simply installing a firewall and antivirus software is not enough to secure a modern network. You must proactively hunt for weaknesses before cybercriminals do. Regular vulnerability assessments and penetration testing are two complementary practices that serve as a crucial "health check" for your security posture, systematically identifying and addressing gaps before they can be exploited. This proactive approach is a cornerstone of effective network security best practices.
A vulnerability assessment acts like a diagnostic scan, using automated tools to identify known security flaws. Penetration testing takes this a step further by simulating a real-world attack. Ethical hackers attempt to actively exploit identified vulnerabilities. A real-world business outcome: a Memphis medical clinic conducted a penetration test and discovered a misconfiguration in their remote access portal. Fixing this flaw prevented a potential HIPAA breach that could have resulted in massive fines and reputational damage.
How Assessments and Testing Work in Practice
These two activities create a powerful feedback loop for continuous security improvement. A vulnerability scan might reveal an unpatched server, while a penetration test could show exactly how an attacker could leverage that server to steal sensitive client data. This provides a clear, risk-based roadmap for remediation and is a core component of IT compliance and risk management.
This proactive approach is so effective that even the Pentagon utilizes it through its "Hack the Pentagon" bug bounty program, which has successfully identified hundreds of critical vulnerabilities by inviting ethical hackers to test their systems.
Actionable Steps for SMBs
For a small or mid-sized business, implementing a robust testing program is more accessible than ever, especially with the help of a professional IT services firm.
- Schedule Regular Scans: Conduct automated vulnerability scans at least monthly. For critical systems like servers holding patient or client data, increase the frequency to weekly.
- Perform Annual Penetration Tests: At a minimum, hire a professional firm for an annual penetration test. For businesses in high-risk sectors like healthcare or legal services, or those managing sensitive financial data, quarterly tests are recommended.
- Test from All Angles: Ensure testing covers both external (internet-facing) and internal perspectives to simulate threats from outside attackers and malicious insiders.
- Prioritize and Remediate: Use the findings to create a prioritized action plan. Focus on fixing vulnerabilities that are easily exploitable and could have a high business impact first, then retest to confirm the fixes are effective.
By integrating these practices, you transform your cybersecurity from a passive defense into an active, intelligence-driven strategy. This not only strengthens your network but also demonstrates a commitment to data protection that builds trust with your clients.
10. Secure Backup and Disaster Recovery Planning
A strong defense isn't enough; you must also be prepared for the moment when a threat breaks through. A secure backup and disaster recovery plan is your ultimate safety net, ensuring your business can survive a catastrophic security incident, system failure, or natural disaster. This practice involves creating secure, isolated copies of your critical data and systems and having a documented, tested plan to restore operations quickly and maintain business continuity.
Without a robust recovery strategy, a single ransomware attack can be an extinction-level event. A real business example: a small manufacturing firm was hit by ransomware that encrypted all their files and their connected backups. Because they had an "air-gapped" (offline) backup as part of their disaster recovery plan, their MSP was able to restore all systems within hours, avoiding a crippling ransom payment and days of downtime. This highlights that simply having backups isn't enough; they must be secure, isolated, and tested.
How Secure Recovery Works in Practice
A modern backup strategy revolves around resilience, particularly against ransomware that actively targets backup files. The goal is to make your data recoverable no matter what happens to your live production environment. The "3-2-1 rule" provides a simple, powerful framework for achieving this resilience. This principle dictates maintaining at least three copies of your data on two different types of media, with one copy stored securely offsite or in the cloud.
This layered approach ensures that a single point of failure, whether a hardware malfunction, a localized disaster, or a malicious attack that encrypts your network, cannot wipe out all your data. By isolating one copy, you create an "air gap" that attackers cannot easily bridge, safeguarding your ability to restore operations.
Actionable Steps for SMBs
For a Dallas or Memphis-based business, implementing a comprehensive business continuity plan is a non-negotiable part of modern IT management.
- Implement the 3-2-1 Rule: Maintain three data copies on two different media types (e.g., local disk and cloud), with one copy stored offsite or in a separate, secure cloud region.
- Use Immutable Backups: Implement backups that cannot be altered, encrypted, or deleted by ransomware for a set period. This is your best defense against backup-targeting malware.
- Test Your Restores: Regularly test your ability to restore data and systems. A backup that has never been tested is not a reliable backup. Schedule quarterly restore drills to validate your plan.
- Isolate Your Backups: Keep backup systems on a segmented network, separate from your primary production environment, to prevent lateral movement from an attacker.
- Encrypt Everything: Ensure all backup data is encrypted both while in transit across the network and at rest in storage.
A well-documented and tested plan is crucial for turning a potential disaster into a manageable inconvenience. To build a resilient strategy tailored to your needs, you can explore professional guidance on data backups and disaster recovery to protect your business assets.
Network Security Best Practices Comparison
Take the Next Step: Partnering for Proactive Security
Navigating the landscape of modern digital threats requires more than a simple checklist; it demands a strategic, multi-layered approach. Throughout this guide, we've detailed ten fundamental network security best practices that form the bedrock of a resilient and secure business environment. From adopting a Zero Trust mindset and implementing robust Multi-Factor Authentication to segmenting your network and conducting regular vulnerability assessments, each practice serves a critical purpose in defending your organization’s most valuable assets.
The core message is clear: proactive defense is always superior to reactive damage control. Implementing the Principle of Least Privilege, encrypting data, and ensuring continuous monitoring are not just technical tasks—they are strategic business decisions. They protect your reputation, ensure compliance (especially for healthcare practices in Dallas and Memphis dealing with HIPAA), and maintain operational continuity. A well-executed backup and disaster recovery plan isn't just an insurance policy; it's a lifeline that guarantees your business can survive unforeseen events, from hardware failure to a sophisticated ransomware attack.
From Theory to Reality: Making Security Actionable
Understanding these concepts is the first step, but consistent implementation is what truly fortifies your defenses. For many small and mid-sized businesses, the challenge lies in managing these complex, interconnected systems while also running daily operations. This is where the gap between knowing what to do and how to do it effectively can widen, leaving dangerous vulnerabilities exposed.
The most important takeaway is that network security is not a one-time project but a continuous process. It requires constant vigilance, specialized expertise, and the right technology stack to keep pace with evolving threats. Without a dedicated team, critical tasks like patch management, security monitoring, and employee training can easily fall behind, creating significant risks.
This is precisely why a partnership with a Managed IT Services provider is no longer a luxury but a strategic necessity. A dedicated partner like PWR Technologies transforms your security posture from a collection of individual tools into a cohesive, managed ecosystem. They bring the expertise needed to implement advanced practices like network micro-segmentation, cloud security for Microsoft 365, and penetration testing, which are often beyond the capacity of in-house teams. For medical clinics and law firms, this partnership ensures that IT systems are not only secure but also fully compliant with stringent industry regulations.
By leveraging proactive IT management, threats are neutralized before they disrupt your operations, and your infrastructure is optimized for performance and growth. This is the ultimate value of mastering these network security best practices: turning your technology from a potential liability into a powerful competitive advantage.
Ready to transform your network from a point of vulnerability into a pillar of strength? The expert team at PWR Technologies LLC specializes in implementing these comprehensive security strategies for businesses across Dallas, TX and Memphis, TN. We provide proactive, responsive managed IT services that align with your specific industry needs, ensuring your operations are secure, compliant, and always running smoothly.




