Endpoint Detection and Response vs Antivirus: A Guide for SMBs
The biggest difference between endpoint detection and response (EDR) and traditional antivirus boils down to one simple concept: antivirus is reactive, while EDR is proactive. Think of it as the difference between a simple gatekeeper checking a pre-approved list versus an active security team patrolling the grounds, looking for any suspicious behavior.
Why Traditional Antivirus Isn't Enough Anymore

For a long time, businesses in Dallas and Memphis got by with standard antivirus (AV) software. It was the digital equivalent of a good front door lock—it did a decent job of keeping common intruders out. But the cyber threats we face today have completely changed the game, and relying on old security tools is like bringing a padlock to a digital heist.
Modern attackers aren't just using old-school viruses anymore. They've moved on to sophisticated tactics like fileless malware, which executes directly in your computer's memory and never touches the hard drive, making it nearly invisible to traditional scans. They also use zero-day exploits to attack security holes that software developers don't even know exist yet.
These advanced methods are specifically designed to slip right past the signature-based detection that old-school AV relies on.
This evolution in attack methods means that a purely reactive security strategy is a recipe for disaster. If you're waiting for a known threat to get flagged, you're giving attackers a huge head start to do real damage.
The New Standard for Endpoint Security
This is where the conversation about endpoint detection and response vs antivirus gets real for business owners. You can't afford not to be proactive. True security now requires deep visibility into what’s happening on every endpoint—every laptop, server, and mobile device—so you can spot the faint signals of an attack before it becomes a full-blown crisis.
A modern layered security plan has to go beyond just blocking known malware. It needs to involve constantly monitoring for unusual behavior and having the right tools—and expertise—to shut it down immediately. To see what a modern defense looks like, you can explore comprehensive cybersecurity and antivirus solutions for Dallas businesses.
To put their differences in perspective, let’s break down how each approach works.
A Quick Look at Antivirus vs EDR
The table below offers an at-a-glance summary of how these two security tools stack up.
As you can see, EDR doesn't just block—it sees, analyzes, and gives a skilled IT partner the power to respond to the full spectrum of modern cyberattacks.
How Traditional Antivirus Works and Where It Falls Short

Think of traditional antivirus (AV) software as a bouncer at a club with a very specific list of troublemakers. Its main job is to check every file that tries to enter your network against this list—a massive database of known malware signatures. Each signature is essentially a unique digital fingerprint left behind by a specific virus or malicious code.
When a file shows up, the AV software quickly scans it. If its fingerprint matches one on the "do not enter" list, the bouncer steps in, either quarantining the file or deleting it on the spot. This method, called signature-based detection, is fantastic at stopping the usual suspects—common viruses, worms, and Trojans that have been making the rounds for years.
For a long time, this was a core part of cybersecurity. It gave businesses a solid first line of defense against predictable attacks, and it still has a place today. The problem is, cybercriminals have gotten much more creative and no longer stick to the old script.
The Limits of a Reactive Model
The fundamental flaw with traditional antivirus is that it's entirely reactive. It can only stop threats it already knows about. This leaves a gaping hole in your defenses when it comes to the new, sophisticated attacks that are now the norm.
Today's cyberattacks have evolved far beyond simple viruses:
- Zero-Day Exploits: These are attacks that target brand-new software vulnerabilities, ones the developers don't even know exist. With no patch available and no signature in the database, a traditional AV is completely defenseless.
- Fileless Malware: This sneaky type of malware doesn't install itself as a file on your hard drive. Instead, it runs directly in your computer’s memory (RAM), leaving no file for a signature-based AV to scan.
- Polymorphic and Metamorphic Malware: Imagine a threat that changes its disguise with every attack. This advanced malware alters its own code to generate a new, unique signature each time it infects a system, making it a moving target that traditional AV can never pin down.
A purely signature-based approach is like trying to catch a master of disguise using a single, outdated photograph. The moment the threat changes its appearance, your security is rendered useless.
A Real-World Scenario: A Dallas Firm's Costly Lesson
Let's look at a mid-sized accounting firm right here in Dallas that learned this lesson the hard way. They were relying on a reputable, well-known antivirus product when they were hit with a polymorphic ransomware attack. The malware was engineered to change its own structure every time it landed on a new machine, creating a fresh signature on each computer.
Because their antivirus was only looking for a single, known fingerprint, it was bypassed entirely. The ransomware spread like wildfire through their network, silently encrypting sensitive client data and critical financial records. By the time anyone noticed, the damage was done. The firm faced crippling downtime, a hefty bill for data recovery, and a serious blow to their clients' trust. This outcome could have been prevented with proactive threat monitoring.
This firm’s story is a stark reminder of the dangerous gap left by a purely reactive security model. If you want to avoid a similar fate, it's worth reading up on how to protect your business against ransomware. It's precisely this kind of gap that modern Endpoint Detection and Response (EDR) solutions are built to close.
Understanding Endpoint Detection and Response

If traditional antivirus is a bouncer checking IDs at the door, think of Endpoint Detection and Response (EDR) as the 24/7 security team monitoring every camera, hallway, and access point inside the building. It’s a completely different philosophy, shifting from a reactive "block the bad guy" stance to a proactive one that actively hunts for threats. EDR doesn’t just wait for known malware to show up; it looks for suspicious behavior across every single one of your endpoints.
This modern approach operates under the assumption that a breach isn't a matter of if, but when. An EDR solution is like having a team of digital forensic experts on staff around the clock. It continuously collects a massive stream of data from every laptop, server, and device—things like process creations, network connections, file modifications, and registry changes.
Using sophisticated behavioral analysis and machine learning, EDR platforms comb through this mountain of data to spot patterns that signal an attack in progress. It isn't looking for a known signature; it's looking for the actions an attacker takes, no matter what tools they're using to do it.
Hunting for Indicators of Compromise
A core function of EDR is its ability to hunt for Indicators of Compromise (IoCs) and, more importantly, Indicators of Attack (IoAs). An IoC might be a malicious file hash—a clear red flag. But an IoA is much more subtle. It's a sequence of seemingly normal actions that, when pieced together, reveal a clear malicious intent.
This is where the line between EDR and antivirus becomes crystal clear. Antivirus is great at blocking known threats based on signatures. EDR, on the other hand, is built for real-time behavioral detection and rapid response, which is why it's so effective against advanced threats like zero-day exploits and fileless malware. For a deeper dive, you can find more on EDR's role compared to traditional AV at BrightDefense.com.
EDR gives you the context to see the entire story of an attack, from how they first got in to how they moved around and tried to steal data.
With EDR, you’re no longer just getting an alert that a bad file was blocked. You’re getting a full forensic timeline that shows you exactly how the attacker got in, what they did, and how to stop them from ever succeeding again.
This deep visibility is a game-changer for incident response. It turns a chaotic guessing game into a precise, data-driven process. Organizations ready for this level of security can learn more about our Endpoint Detection and Response services in Dallas.
A Practical Example: A Memphis Business Averts Disaster
Picture a logistics company in Memphis where operations rely on constant uptime and real-time data. One night, their Managed IT provider noticed a series of strange activities coming from an employee’s workstation. A traditional antivirus scan came up completely clean—no malicious files were found.
But their EDR solution told a different story. It flagged the behavior as highly suspicious, detecting that PowerShell—a legitimate and powerful system administration tool—was being used to download scripts from an unknown server and access sensitive network files. The attacker was "living off the land," using the system's own tools to fly under the radar.
The EDR platform immediately alerted the security team and laid out the entire attack chain:
- An employee clicked a deceptive link in a phishing email.
- This triggered a script that launched a hidden PowerShell session.
- The attacker then used that session to start moving laterally across the network.
Because the EDR system caught this strange behavior in its earliest stages, the security team was able to isolate the compromised endpoint and kill the malicious processes before any data was stolen or encrypted. This real-world scenario perfectly illustrates the crucial difference in the endpoint detection and response vs antivirus debate—EDR sees the stealthy attacks that AV was never designed to catch.
Comparing Critical Security Capabilities
When you stack Endpoint Detection and Response (EDR) up against a traditional antivirus, the differences become much clearer than just "proactive vs. reactive." The real gap is in how each tool sees, interprets, and acts on potential threats. For a small business, getting this distinction right is crucial to choosing a solution that truly protects your operations.
Let's dig into the core functions where these two security tools really go their separate ways.
Threat Detection Methods
Traditional antivirus works almost entirely on signature-based detection. Think of it like a bouncer with a list of known troublemakers at the door. If a file’s digital fingerprint matches a known virus, it gets blocked. This approach is still effective for stopping common, well-documented malware.
EDR, on the other hand, uses behavioral analysis. It's more like a seasoned security guard who doesn't just check IDs but watches for suspicious actions. They're looking for someone loitering, rattling door handles, or hiding in the shadows—actions that are red flags regardless of who the person is. This allows EDR to catch brand-new threats, including zero-day attacks and fileless malware that have no signature.
While antivirus answers the question, “Is this file on my blacklist?” EDR answers a much more powerful one: “Is this activity normal for my environment, or could it be part of an attack?”
This difference in detection is fundamental. In fact, the growing complexity of cyber threats is a key driver behind the rapid expansion of the global EDR market. Valued at over $7 billion in 2023, it's projected to grow at a CAGR of over 25%—a clear signal that businesses need more advanced, behavior-based threat detection.
Scope of Protection
The scope of what each tool protects is a direct result of its detection method. A traditional AV is limited to its library of known threats. It’s a valuable layer of defense against the everyday viruses and worms still making the rounds, but its protective bubble ends there.
EDR's scope is far broader because it's built to handle the unknown. Since it monitors endpoint behavior, it can spot and stop sophisticated attacks that traditional AV is completely blind to.
This includes things like:
- Living-off-the-land attacks, where intruders use legitimate system tools like PowerShell to carry out malicious activities.
- Credential theft, where attackers try to steal usernames and passwords directly from memory.
- Lateral movement, where an attacker who has compromised one machine attempts to spread to others across your network.
By focusing on the techniques of an attack rather than just the specific malware, EDR provides a much more resilient defense. One of its most critical capabilities is providing robust ransomware defense, as it can detect the encryption behaviors common to all ransomware attacks, even brand-new variants.
Response Actions
When an antivirus solution finds a threat, its response is simple and automatic: quarantine or delete. The malicious file gets locked away to prevent it from causing harm. While this works for simple threats, it offers zero context about how the threat got there in the first place.
EDR gives your IT partner a full suite of remediation and response tools. Instead of just deleting a file, a security analyst can take direct action.
They can:
- Isolate the endpoint: Immediately disconnect a compromised device from the network to stop an attack from spreading.
- Terminate malicious processes: Kill active threats that are running in the system’s memory.
- Roll back changes: Some advanced EDR tools can even reverse malicious changes, like restoring files that were encrypted by ransomware.
This ability to take precise, surgical action during a live incident is a game-changer. It’s the difference between just treating a symptom and actually curing the disease.
Investigation and Visibility
Perhaps the most profound advantage of EDR is the deep visibility it provides. An alert from an antivirus product is usually just a simple notification: "Malicious file found and blocked." It tells you what happened, but not why or how.
An EDR platform, in contrast, gives you a complete forensic record. It logs all endpoint activities, allowing security professionals to trace the entire lifecycle of an attack—often called the "attack chain."
While antivirus simply tells you if a known file was blocked, EDR shows you the entire story of an attack—how it began, what systems it touched, and how to prevent it from happening again.
This level of detail is invaluable. It helps you understand your security weaknesses, close vulnerabilities, and strengthen your overall defenses over time. It’s a core component of strong network security best practices because it provides the intelligence you need to prevent future incidents, not just clean up the current one.
Feature Breakdown Antivirus vs EDR
To really see the difference in action, it helps to break down the features side-by-side. The table below illustrates how each tool approaches key security functions and why those differences matter for a business trying to defend against modern threats.
As you can see, EDR isn't just an upgraded antivirus—it’s a fundamentally different approach to security. It assumes that a breach is not a matter of if but when, and it gives you the tools to find, fight, and fix the problem quickly.
When Is EDR the Right Choice for Your Business
Choosing between endpoint detection and response (EDR) and traditional antivirus isn't just a simple upgrade—it's a strategic move based on your company's risk profile. While antivirus software provides a solid foundation, some situations demand the kind of proactive, deep-dive visibility you only get from an EDR solution. If any of the following scenarios sound familiar, EDR is no longer a "nice-to-have" but a core business necessity.
Businesses Handling Sensitive or Regulated Data
For companies in Dallas and Memphis that manage sensitive client data—think medical practices governed by HIPAA, financial firms under GLBA, or retailers handling credit card information under PCI DSS—the stakes couldn't be higher. A data breach is more than just an IT headache; it's a massive compliance failure that can trigger crippling fines, legal battles, and permanently damage customer trust.
A standard antivirus can catch known malware, but it's practically blind to the stealthy, targeted attacks designed to steal specific types of data. EDR, on the other hand, provides the constant monitoring and behavioral analysis needed to spot an intruder trying to access protected health information (PHI) or cardholder data. It stops them in their tracks before a reportable breach occurs, a proactive posture that’s essential for staying compliant.
This infographic gives a great side-by-side look at how antivirus and EDR tackle security.
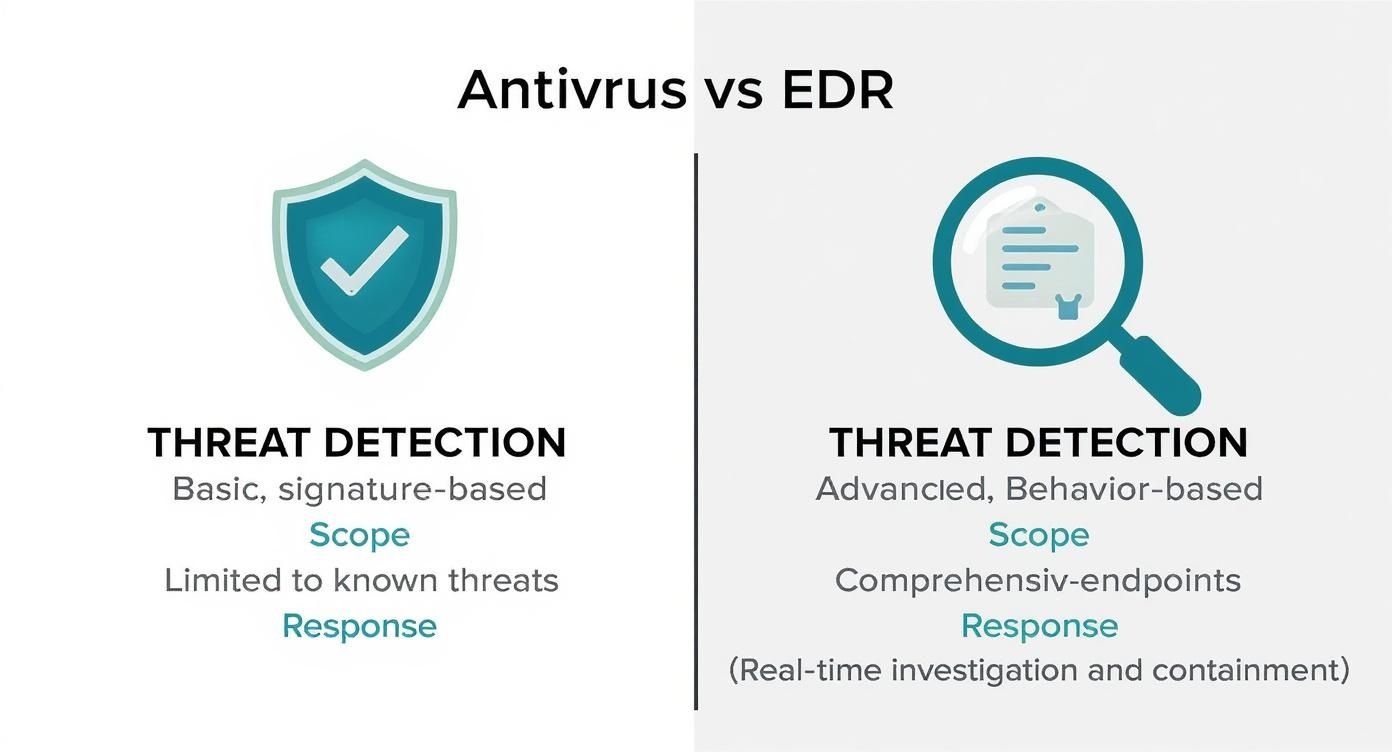
As you can see, antivirus has a narrow focus on known threats. EDR provides the comprehensive visibility and response needed to handle the unknown.
Companies with Remote or Hybrid Workforces
The old office perimeter has all but vanished with the rise of remote work. When your team is working from home, their laptops are outside the corporate firewall, opening up countless new entry points for attackers. Antivirus by itself just isn't enough to secure such a spread-out environment.
This is exactly the reality EDR was built for. It essentially puts a security analyst on every single endpoint, regardless of its physical location. This capability is shaking up the market, with a majority of EDR solutions now being cloud-based to support distributed teams. These platforms make sure every employee device is monitored for suspicious activity, protecting your organization from threats that start miles away from the office.
Of course, you have to think about the practical side of getting it installed and managed across a distributed team. Leveraging automated deployment tools like Microsoft Intune can make the rollout process much smoother.
For a hybrid workforce, EDR is the security backbone that connects and protects every team member, ensuring that a compromised home network doesn't become a catastrophic business breach.
Organizations Previously Targeted by Advanced Attacks
Has your business ever been hit by a phishing scam, a social engineering trick, or a breach that your antivirus completely missed? That's a huge red flag telling you that your current defenses aren't cutting it. Attackers are notorious for revisiting targets they know are easy pickings. Sticking with the same security that already failed is just asking for another incident.
EDR offers the advanced threat-hunting tools you need to break that cycle. It spots the subtle clues of an attack in progress, like a user’s machine suddenly executing strange scripts or trying to access sensitive files it shouldn't. By catching and stopping these actions in real time, EDR can prevent a single clicked phishing link from spiraling into a company-wide ransomware disaster. Implementing EDR is a sign of a mature security strategy, and it's often best handled through managed security services that bring the expertise needed to run the tool effectively.
Getting the Most Out of EDR with Managed Services
While EDR technology is incredibly powerful, it's nothing like the "set it and forget it" antivirus programs we're used to. Its real strength comes from the security experts who manage it. EDR platforms are designed to generate a ton of data and alerts, and every single one needs to be analyzed quickly and correctly to tell a real threat from harmless background noise.
For most small and mid-sized businesses, building an in-house team of security analysts to monitor an EDR solution 24/7 just isn’t practical. This is where partnering with a Managed IT Services Provider (MSP) can be a game-changer, turning a complicated tool into a simple, effective security solution.
How an MSP Manages Your EDR
A good MSP basically becomes your dedicated Security Operations Center (SOC). Instead of leaving you to figure out what a complex alert means, the MSP manages the entire endpoint security process from start to finish. This hands-on approach ensures your investment in EDR technology actually delivers real protection and peace of mind.
A managed EDR service from an MSP usually covers:
- Expert Setup and Fine-Tuning: The MSP will install and configure the EDR agent for your specific IT environment, adjusting its rules to catch as many threats as possible while cutting down on false alarms.
- 24/7 Monitoring and Alert Triage: A team of security pros keeps a constant watch on EDR alerts. They investigate anything that looks suspicious so your team doesn't have to sift through the noise.
- Threat Investigation and Analysis: When a legitimate threat pops up, the MSP’s experts dig in to understand the entire attack—how it started, what files or systems it touched, and the best way to shut it down.
- Rapid Incident Response: The MSP jumps into action immediately to neutralize threats. This could mean isolating a compromised laptop from the network or killing a malicious process before it can spread and cause real damage.
Partnering with an MSP for EDR gives your business the kind of high-level threat hunting and response capabilities that used to be reserved for large enterprises, all without the six-figure cost of hiring an in-house security team.
Turning Technology into Real-World Security
Think about a property management company here in Dallas that we helped switch to EDR. At first, their one-person IT department was completely swamped, getting thousands of alerts a day and having no idea which ones were urgent. After they partnered with PWR Technologies, that firehose of raw data turned into clear, actionable intelligence.
Our team took over the monitoring, filtering out all the noise and only escalating true security incidents. When a hacker tried to use a legitimate IT tool to take over a server, we didn't just get an alert—we saw the entire attack unfold, isolated the machine in minutes, and stopped a major breach before it happened. That’s the real difference between just having EDR and having a managed security service that knows how to use it.
Answering Your Questions About EDR and Antivirus
It’s only natural to have questions when you’re thinking about moving from a familiar tool like antivirus to a more robust solution like Endpoint Detection and Response (EDR). For small business owners, getting straight answers on the practical side of things is what matters most. Here are the questions we hear most often from businesses in Dallas and Memphis.
Does EDR completely replace my current antivirus?
Yes, for all practical purposes, it does. Modern EDR solutions are typically built into what’s called a Next-Generation Antivirus (NGAV) platform. This means you get the best of both worlds in one package: classic signature-based scanning for known viruses and the sophisticated behavioral analysis needed to stop new, unknown threats.
Because this is an all-in-one approach, you end up with a single, lightweight agent on your computers. Your old, traditional antivirus program is no longer needed, which is great because it simplifies management and reduces software bloat on your systems.
Isn't EDR too expensive for a small business?
While EDR costs more upfront than a basic antivirus subscription, its real worth comes from risk reduction. Think about the cost of just one successful security breach. You’re looking at downtime, data recovery expenses, potential fines, and a hit to your reputation that can be devastating for a small business. That one event will almost always cost far more than the investment in proper EDR protection.
When you get EDR through a managed IT service provider, it’s not a huge capital expense. It becomes a predictable monthly operational cost that delivers enterprise-level security without the sticker shock of hiring an in-house security team.
My company is small—why would hackers even target us?
This is one of the most dangerous myths out there. Hackers love targeting small businesses for that exact reason—they assume your defenses are weaker. SMBs are often viewed as a soft target or an easy backdoor into the systems of their larger clients and partners.
Cybercriminals aren't hand-picking targets one by one. They use automated bots that constantly scour the internet for any vulnerability they can find. Your size doesn't matter to them; if you're online, you're on their radar.
How much work is it to actually manage an EDR solution?
If you try to do it yourself without a dedicated cybersecurity expert on staff, it's a massive undertaking. A proper EDR system requires 24/7 monitoring and someone with the right skills to immediately investigate every single alert. It's a full-time job, and then some.
This is exactly why most SMBs partner with a Managed Services Provider (MSP). The MSP’s security operations team takes care of all the heavy lifting behind the scenes. They sift through the noise, handle the real threats, and let you get back to what you do best—running your business.
Ready to move beyond basic antivirus and secure your business with proactive threat detection? The team at PWR Technologies can manage a powerful EDR solution tailored for your business, giving you enterprise-grade protection without the complexity. Contact us today to learn how we protect businesses in Dallas and Memphis.




