12 Best Multi-Factor Authentication Solutions for SMBs
In today's threat landscape, a simple password is no longer enough to protect your business's critical data. Cybercriminals relentlessly target small and mid-sized businesses in Dallas and Memphis, exploiting weak credentials to gain access to sensitive information. This is where Multi-Factor Authentication (MFA) becomes a non-negotiable layer of your cybersecurity strategy, making it significantly harder for unauthorized users to breach your defenses.
Implementing a robust MFA solution is a fundamental step in proactive IT management that safeguards your operations and ensures business continuity. For a growing Dallas-based accounting firm, a sophisticated phishing attack was thwarted because their managed IT provider had implemented MFA across their Microsoft 365 environment. The attacker stole a password but was stopped cold at the second verification step, preventing a data breach that could have violated client trust and led to regulatory fines. This real-world example demonstrates why MFA is a foundational defense. This guide cuts through the noise to help you find the best multi-factor authentication solutions for your specific needs, whether you're a medical practice requiring HIPAA compliance or a professional services firm aiming to reduce downtime.
We will review and compare top MFA tools like Okta, Cisco Duo, and Microsoft Entra ID, providing a detailed analysis of their features, pricing, and implementation considerations. Each entry includes direct links and screenshots to help you make an informed decision that aligns with your security requirements and budget, securing your company's future.
1. Okta (Workforce Identity Cloud – Adaptive MFA)
Okta stands as a leader in the identity management space, making it one of the best multi-factor authentication solutions for businesses scaling from small operations to enterprise-level complexity. It excels with its extensive library of over 7,000 pre-built integrations, allowing businesses in Dallas and Memphis to secure almost any application in their tech stack, from Microsoft 365 to custom internal tools. A co-managed IT partnership often leverages Okta to unify access control for a client’s internal IT team, streamlining security across both cloud and legacy applications.
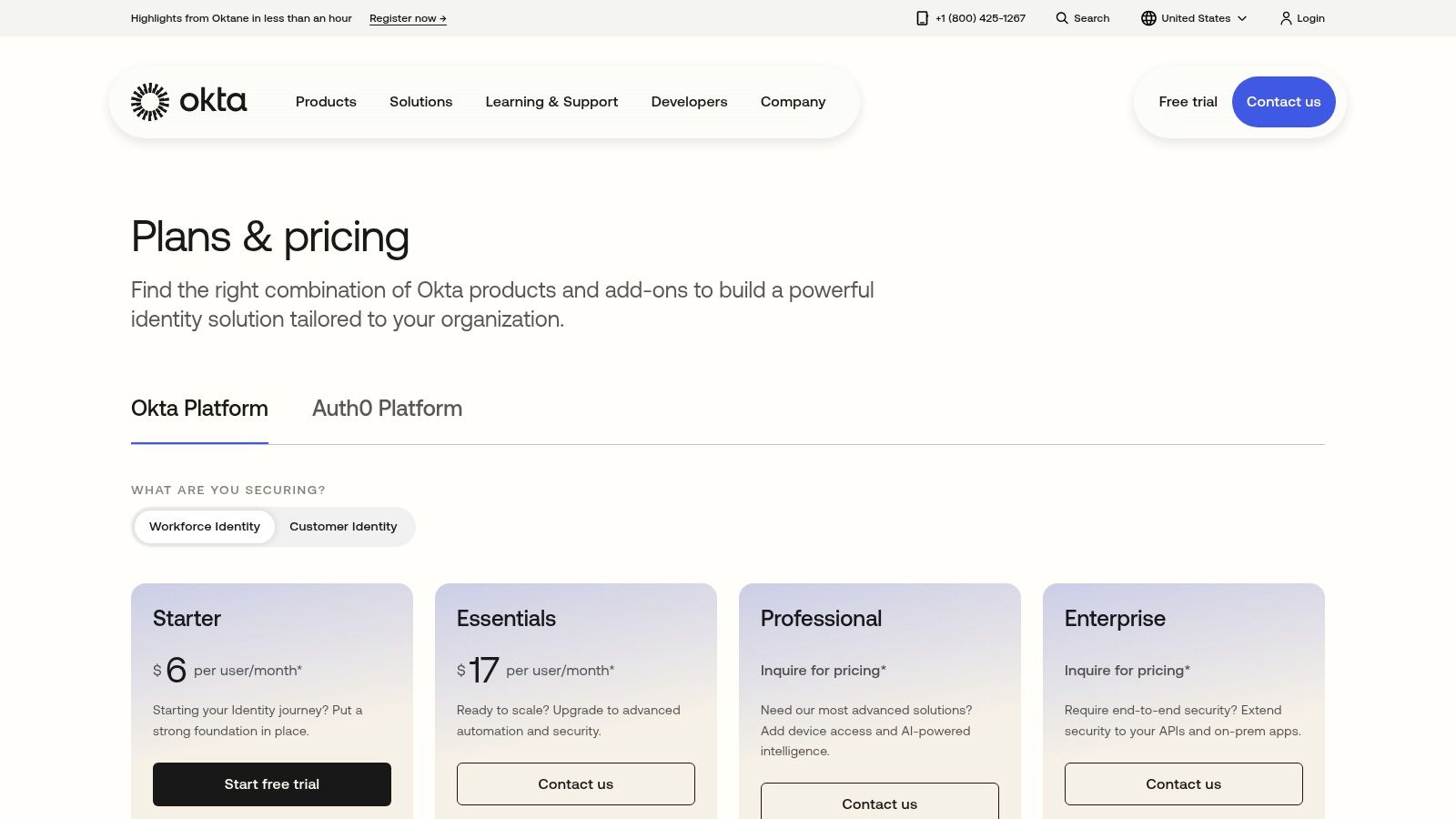
Okta’s Adaptive MFA, available in higher tiers, leverages contextual signals like device posture, user location, and network reputation to challenge high-risk logins while providing a frictionless experience for legitimate users. This intelligent approach aligns perfectly with modern cybersecurity frameworks like Zero Trust, which assumes no user or device is inherently trustworthy. By evaluating risk in real-time, Okta helps implement a core component of a modern security posture. Learn more about Zero Trust security and how adaptive policies strengthen your defenses.
Key Details & Use Case
- Best For: Businesses in regulated industries like healthcare or finance needing extensive app compatibility and adaptive, risk-based authentication policies.
- Pros: Strong phishing-resistant options (Okta FastPass, FIDO2), transparent suite-based pricing with a free trial, and excellent documentation for IT teams.
- Cons: Advanced features require higher-tier plans, which can become costly. The suite matrix can be complex to navigate, often necessitating consultation with an IT partner.
- Website: https://www.okta.com/pricing/
2. Cisco Duo
Cisco Duo is renowned for its user-friendly approach, making it one of the best multi-factor authentication solutions for businesses prioritizing a smooth and rapid rollout. It simplifies security for organizations with its intuitive Duo Mobile push notifications, which offer a near-frictionless verification experience for employees. For example, a Memphis-based law firm was able to deploy Duo to all its attorneys and staff in a single afternoon with minimal training, immediately securing access to their sensitive case management system.

The platform’s strength lies in its accessibility and tiered plans, including a free edition for up to 10 users, making it ideal for startups or small businesses testing MFA adoption. As organizations grow, Duo’s higher-tier plans introduce adaptive, risk-based policies and device trust capabilities. These features ensure that only healthy, trusted endpoints can access sensitive applications, a crucial element in a layered security strategy. By verifying device posture before granting access, Duo helps enforce key network security best practices to protect company data.
Key Details & Use Case
- Best For: Small to mid-sized businesses and organizations seeking a straightforward, highly-rated MFA solution that is easy to deploy and manage.
- Pros: Extremely easy rollout with a 30-day free trial, widely recognized and trusted (Gartner Peer Insights Customers’ Choice), and competitive entry-level pricing.
- Cons: Advanced risk signals and trust features are locked behind higher-tier plans, and physical hardware tokens must be purchased separately.
- Website: https://duo.com/editions-and-pricing
3. Microsoft Entra ID (Azure AD)
For organizations deeply invested in the Microsoft ecosystem, Microsoft Entra ID (formerly Azure AD) is one of the best multi-factor authentication solutions available due to its native integration. It secures access to Microsoft 365 and Azure resources with a range of methods, including the Microsoft Authenticator app, FIDO2/passkeys, and Windows Hello for Business. This makes it a natural and streamlined choice for businesses in Dallas and Memphis already using Microsoft's cloud solutions for collaboration and productivity.
While baseline MFA is included with many Microsoft 365 plans through "security defaults," its true power is unlocked with Conditional Access policies available in P1 or P2 licenses. These policies allow IT administrators to create granular rules that challenge users based on location, device compliance, or sign-in risk. A managed IT service provider can configure these policies to, for example, block logins from outside the U.S. or require MFA for any access attempt from an unmanaged personal device, significantly strengthening an organization's security posture. Learn more about professional Microsoft 365 optimization to ensure your tenant is fully protected.
Key Details & Use Case
- Best For: Small to enterprise-level businesses that heavily rely on Microsoft 365, Azure, and Windows environments for their daily operations.
- Pros: Tightly integrated with the Microsoft ecosystem, strong phishing-resistant options (Windows Hello, FIDO2), and centralized administration within the Azure portal.
- Cons: Advanced Conditional Access policies and enhanced reporting require pricier Entra ID P1 or P2 licenses, and the licensing structure can be complex.
- Website: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings
4. Google Cloud Identity & Identity Platform
For businesses deeply integrated into the Google ecosystem or developers building custom applications, Google offers one of the best multi-factor authentication solutions split into two distinct tracks. Cloud Identity provides workforce authentication for employees accessing Google Workspace and other cloud apps, while Identity Platform is a customer-facing identity (CIAM) solution. This dual approach gives Dallas-area businesses flexibility, whether they're securing internal teams or building secure customer-facing applications.
The platform stands out with its developer-friendly tools and a transparent, usage-based pricing model, particularly for its Identity Platform. This allows startups and scaling businesses to implement robust MFA, including FIDO2 and Google Authenticator, without significant upfront costs. For instance, a tech startup could integrate secure logins into their new mobile app for thousands of users at a very low initial cost, tying security expenses directly to business growth. This makes it an attractive choice for modern, cloud-native operations.
Key Details & Use Case
- Best For: Developers and startups needing a scalable, API-driven CIAM solution, or organizations heavily invested in the Google Workspace and Cloud ecosystem.
- Pros: Flexible MAU-based pricing with generous free tiers, strong developer tooling, and seamless integration with Google’s administrative and cloud infrastructure.
- Cons: Per-event SMS/phone verification costs can accumulate at scale, and accessing advanced workforce features may require upgrading to a paid Cloud Identity or Workspace plan.
- Website: https://cloud.google.com/identity/pricing
5. Auth0 (by Okta)
While Okta excels at workforce identity, its Auth0 platform is purpose-built for developers adding authentication to customer-facing applications, making it one of the best multi-factor authentication solutions for businesses building custom software. Auth0 provides a highly flexible, API-first approach, allowing development teams in Dallas and Memphis to quickly integrate secure login and MFA into their products. It shines by offering a comprehensive toolkit that balances robust security with a customizable user experience.
Auth0’s power lies in its developer-centric design, providing SDKs and a Universal Login feature that simplifies implementation. A software company launching a new SaaS product could use Auth0 to offer their customers login options via social accounts (like Google or LinkedIn) and enforce MFA with push notifications, all while branding the login page to match their application perfectly. This focus on seamless integration reduces both development time and initial costs.
Key Details & Use Case
- Best For: Developers and businesses needing to embed a highly customizable and scalable MFA solution directly into their customer-facing applications and digital products.
- Pros: Excellent developer documentation and quick-start guides, a generous free plan with high monthly active user (MAU) limits for prototyping, and easy branding for login pages.
- Cons: Adaptive MFA and certain advanced factors are locked behind higher-priced enterprise plans, and per-message SMS costs can unexpectedly increase the total cost of ownership.
- Website: https://auth0.com/docs/secure/multi-factor-authentication
6. Ping Identity (PingOne MFA / PingID)
Ping Identity is an enterprise-grade solution well-suited for organizations with complex, hybrid IT environments. It offers distinct MFA products: PingID for securing the workforce and PingOne MFA for protecting customer-facing web and mobile applications. This dual focus makes it one of the best multi-factor authentication solutions for Dallas businesses managing both internal and external user access securely. Its ability to deploy in a flexible SaaS or hybrid model is essential for companies with significant on-premise infrastructure that are migrating to the cloud.
Ping Identity excels with adaptive, risk-based policies that evaluate contextual signals to determine when to prompt for additional verification, creating a secure yet seamless user experience. For example, a financial services firm could use Ping to allow frictionless access for employees on the corporate network but require MFA for any login attempt from an unrecognized device or location. This robust feature set ensures comprehensive protection across diverse and demanding IT landscapes.
Key Details & Use Case
- Best For: Enterprises and mid-sized businesses with hybrid IT environments (on-premises and cloud) needing a unified MFA solution for both workforce and customer identity.
- Pros: Excellent for complex enterprise deployments, strong integration with Ping's SSO and federation services, and extensive documentation for IT administrators.
- Cons: Pricing typically requires a direct sales consultation, and its enterprise focus may be overly complex and costly for smaller teams or simple use cases.
- Website: https://www.pingidentity.com/en/platform/capabilities/multi-factor-authentication/pingone-mfa.html
7. Yubico (YubiKey hardware security keys)
Yubico shifts the focus from software-based MFA to robust, phishing-resistant hardware authentication. The company's YubiKeys are physical security keys that provide a tangible second factor, making them one of the best multi-factor authentication solutions for organizations prioritizing the highest level of account security. A Dallas-area healthcare provider, for instance, equipped its doctors with YubiKeys to meet strict HIPAA compliance requirements for accessing electronic health records (EHR), ensuring that patient data is protected by the strongest possible authentication method.
By leveraging standards like FIDO2/WebAuthn, YubiKeys offer a superior defense against phishing attacks that can bypass codes sent via SMS or email. This physical, "something you have" factor is a cornerstone of a modern Zero Trust security model. Implementing hardware keys is a practical step toward a stronger defense posture. Find out more about how to implement Zero Trust security and where hardware tokens fit in.
Key Details & Use Case
- Best For: Healthcare clinics, legal firms, and any business needing to meet strict compliance requirements or secure high-value accounts with phishing-proof hardware.
- Pros: Industry-standard hardware with broad service and platform support, durable form factors (USB-A/C, NFC), and enterprise-grade certification options (FIPS).
- Cons: Requires an up-front hardware cost per user, and it is a best practice to purchase a spare key for each employee, adding to the initial investment.
- Website: https://www.yubico.com/products/yubikey-5-overview/
8. Amazon (marketplace for FIDO2/MFA hardware keys)
While not a software solution itself, Amazon serves a crucial role as an accessible marketplace for procuring some of the best multi-factor authentication hardware. For businesses in Dallas and Memphis needing to implement phishing-resistant MFA, Amazon provides a fast and reliable channel to purchase physical security keys from top brands like Yubico, Feitian, and Thetis. This is particularly useful for deploying FIDO2/U2F keys, which offer the strongest protection against credential theft as part of an endpoint management strategy.
A managed IT provider can use their Amazon Business account to quickly order a batch of security keys for a new client onboarding, ensuring every employee is equipped from day one without long procurement delays. The platform's value lies in its wide selection, competitive pricing, and rapid fulfillment. User reviews and Q&A sections also provide valuable real-world insights into device compatibility and durability, helping organizations make informed purchasing decisions.
Key Details & Use Case
- Best For: Businesses of all sizes needing rapid procurement of FIDO2/U2F hardware keys for deploying phishing-resistant MFA across their teams.
- Pros: Fast Prime shipping and straightforward returns, a huge variety of models from different brands, and user reviews to guide purchasing decisions.
- Cons: Buyers must be vigilant in verifying sellers to avoid counterfeit products or units with outdated firmware. It's best to purchase directly from official brand storefronts on the site.
- Website: https://www.amazon.com/s?k=fido2+security+key
9. Best Buy (retailer for security keys)
While not a software solution, Best Buy serves a critical role for businesses needing immediate access to high-quality MFA hardware. As an authorized retailer for top brands like YubiKey, it provides a convenient and trustworthy channel for businesses in Dallas and Memphis to procure physical security keys without waiting for shipping. This is especially useful for small teams or individuals needing to quickly replace a lost key or outfit a new employee to maintain security compliance.
Imagine an employee loses their security key right before an important deadline. A quick trip to a local Best Buy allows an IT manager to pick up a replacement the same day, preventing downtime and ensuring business continuity. The primary advantage is this local availability and ease of returns. This accessibility makes it one of the best multi-factor authentication solutions for teams that value speed and convenience for sourcing phishing-resistant hardware, a cornerstone of any robust endpoint security strategy.
Key Details & Use Case
- Best For: Small businesses, IT consultants, or individuals needing same-day access to physical security keys like YubiKeys for immediate deployment or replacement.
- Pros: Convenient same-day curbside pickup, easy in-person returns and warranty handling, and access to retail promotions and sales on security hardware.
- Cons: The selection is much narrower than purchasing directly from vendors or specialized online stores. Stock and model availability can vary significantly by store location.
- Website: https://www.bestbuy.com/site/shop/security-key-two-factor-authentication
10. FIDO Alliance (Certified Products Directory)
While not a direct provider, the FIDO Alliance website is an indispensable resource for any Dallas or Memphis business committed to implementing the strongest form of MFA. It serves as the official, authoritative directory of all FIDO-certified products, including security keys and software authenticators. For companies vetting hardware or software solutions, this directory is the definitive source to confirm that a potential vendor’s claims of FIDO2 or WebAuthn compliance are legitimate and have been independently verified.
Using this resource ensures that your procurement process is grounded in verified standards, significantly reducing the risk of purchasing non-compliant or insecure hardware. This is a critical step in IT risk management, especially for organizations in regulated sectors that need to prove they are deploying phishing-resistant MFA as part of their cybersecurity and compliance frameworks. It transforms vendor selection from a guessing game into a straightforward verification process, making it one of the best multi-factor authentication solutions for due diligence.
Key Details & Use Case
- Best For: IT managers, procurement teams, and compliance officers needing to verify that hardware or software authenticators meet FIDO standards for phishing resistance.
- Pros: Authoritative and globally recognized source for certification, helps mitigate procurement risks, and is a completely free and accessible resource.
- Cons: It is a directory, not a storefront, so you must purchase products from the vendors directly. The technical metadata can be dense for non-specialists.
- Website: https://fidoalliance.org/certification/fido-certified-products/
11. G2 (Multi‑Factor Authentication category)
Instead of a single product, G2 offers a comprehensive starting point for Dallas-Fort Worth businesses evaluating the crowded market of MFA solutions. It acts as a live, user-driven research hub, aggregating hundreds of peer reviews, feature comparisons, and satisfaction ratings across dozens of vendors. This approach allows businesses to quickly understand the real-world performance and user experience of different platforms before committing to a demo.
G2's platform allows you to filter the best multi-factor authentication solutions by specific capabilities, such as support for push notifications, biometrics, or risk-based policies. This feature-level sorting is invaluable for creating a shortlist of vendors that meet your exact technical and compliance requirements. For businesses unsure where to begin their security journey, using a platform like G2 can simplify the initial vendor discovery process, which is a key function often handled by a managed IT service provider. Learn more about what managed service providers do to help businesses select and implement the right security tools.
Key Details & Use Case
- Best For: Businesses in the initial research phase looking to compare top-rated MFA solutions based on verified user reviews and specific feature requirements.
- Pros: Excellent for shortlisting vendors based on peer feedback, feature-level filtering accelerates evaluation, and the content is free to browse and frequently updated.
- Cons: Sponsored placements can appear at the top of lists, so it's wise to verify details directly on vendor sites. Some reviews may lack deep technical context for complex use cases.
- Website: https://www.g2.com/categories/multi-factor-authentication-mfa
12. RSA SecurID
RSA SecurID is one of the most established names in enterprise security, offering some of the best multi-factor authentication solutions for complex or highly regulated environments. Known for its iconic hardware tokens, the platform has evolved to include mobile authenticators, FIDO2 support, and biometrics. Its primary strength lies in its flexible deployment options, supporting on-premises, hybrid, and cloud-based models, making it ideal for Dallas-area businesses with significant legacy infrastructure like VPNs or on-premise enterprise applications.
This versatility makes RSA SecurID a powerful choice for organizations in finance or healthcare that cannot move fully to the cloud but still need to secure modern SaaS applications alongside their traditional systems. For example, a bank could use RSA to secure both its legacy mainframe access for tellers and its new cloud-based CRM for loan officers. By bridging the gap between old and new systems, it offers a pragmatic path to stronger, more unified IT security.
Key Details & Use Case
- Best For: Enterprises and regulated businesses needing to integrate modern MFA with legacy on-premise systems, such as VPNs, servers, and network devices.
- Pros: Excellent support for hybrid environments, a wide range of authenticator options (hardware and software), and a strong reputation for enterprise-grade security and reliability.
- Cons: Pricing is complex and typically requires a direct sales quote; implementation can be more intensive and costly compared to pure cloud-native solutions.
- Website: https://www.rsa.com/products/securid/
Top 12 MFA Solutions Comparison
Secure Your Business with Expert MFA Implementation
Navigating the landscape of multi-factor authentication can feel complex, but the path to securing your business is clearer than it appears. We've explored a wide spectrum of the best multi-factor authentication solutions, from comprehensive cloud identity platforms like Okta and Microsoft Entra ID to the physical, phishing-resistant security of YubiKey hardware tokens. Each tool offers a unique balance of security, user experience, and administrative control, underscoring a critical truth: there is no one-size-fits-all answer.
Your ideal solution depends entirely on your specific operational needs, compliance requirements, and existing technology stack. A Dallas-based medical clinic with strict HIPAA mandates will prioritize different features than a professional services firm in Memphis looking to secure its Microsoft 365 environment. The former might lean towards Cisco Duo for its robust device trust policies, while the latter will find immense value in the seamless integration offered by Microsoft Entra ID.
Key Takeaways and Actionable Next Steps
Making the right choice is the first step, but flawless implementation is what truly hardens your defenses. A poorly configured MFA system can create security gaps or frustrate employees, undermining its purpose and leading to costly downtime.
To move forward effectively, consider these crucial factors:
- Assess Your Current Environment: Which applications and systems need protection? Do you operate primarily in the cloud, on-premises, or in a hybrid model? This infrastructure assessment is key.
- Evaluate User Experience: How will your team interact with the MFA solution? The most secure system is useless if employees bypass it due to inconvenience. Options like push notifications are generally more user-friendly than one-time passcodes and are essential for security awareness.
- Consider Compliance and Risk: Do you handle sensitive data subject to regulations like HIPAA or PCI DSS? Your choice must align with these legal and industry standards as part of a comprehensive risk management plan.
- Plan for Scalability: Select a solution that can grow with your business, accommodating new users, applications, and evolving security threats without requiring a complete overhaul.
For instance, a growing property management company in the Dallas-Fort Worth area successfully deployed Cisco Duo with the help of a managed IT service provider. This proactive step secured remote access for their agents without disrupting workflow. When a phishing attempt targeted an agent's email, the mandatory MFA prompt blocked the unauthorized login, preventing a breach that could have led to significant financial and reputational damage. This real-world scenario highlights how expert implementation turns a security tool into a tangible business asset.
Choosing and implementing one of the best multi-factor authentication solutions is a foundational pillar of modern cybersecurity and business continuity. It’s an investment not just in technology, but in the trust of your clients, the productivity of your team, and the long-term resilience of your business. By taking a strategic, well-guided approach, you can transform this essential security measure from a complex challenge into a powerful competitive advantage.
Ready to move beyond an article and implement a tailored security strategy? PWR Technologies LLC specializes in helping small and mid-sized businesses in Dallas and Memphis select, deploy, and manage the right MFA solutions to protect their critical assets. Partner with us for proactive IT support to ensure your security is seamless, compliant, and ready for whatever comes next. Learn more about our managed IT security services.




